- 10 High-Risk Vulnerabilities
- 1. Langflow Unauthorized Code Injection Vulnerability (CVE-2025-3248)
- 2. Microsoft SharePoint Server RCE Exploit Chain (CVE-2025-53770, CVE-2025-53771)
- 3. Sudo Improper External Resource Reference Vulnerability (CVE-2025-32463)
- 4. Docker Desktop Inadequate Access Control Vulnerability (CVE-2025-9074)
- 5. Combined Exploit Chain: WhatsApp Authorization Validation Vulnerability and Apple Image I/O Out-of-Bounds Write (CVE-2025-55177, CVE-2025-43300)
- 6. SGLang Large Model Inference Framework Remote Code Execution (CVE-2025-10164)
- 7. Unitree Robot BLE Vulnerabilities (CVE-2025-35027, CVE-2025-60250, CVE-2025-60251)
- 8. FortiWeb Remote Code Execution Vulnerability Chain (CVE-2025-64446, CVE-2025-58034)
- 9. Samsung Mobile Device Quram Image Parsing Library Remote Code Execution (CVE-2025-21042)
- 10. React Server Components Code Injection Vulnerability (CVE-2025-55182)
- MongoBleed Vulnerability (CVE-2025-14847)
The cybersecurity landscape in 2025 has been marked by an unprecedented surge in critical vulnerabilities, with over 21,500 CVEs disclosed in the first half of the year alone, representing a 16-18% increase compared to 2024.
Among these, a select group of vulnerabilities stands out due to their exceptional severity, active exploitation in the wild, and potential for enterprise-wide compromise.
This comprehensive analysis examines the ten most significant high-risk vulnerabilities of 2025, detailing their technical mechanisms, real-world impact, and implications for organizations worldwide.
10 High-Risk Vulnerabilities
| Vulnerability & CVE | Severity | Attack Vector | Authentication | Key Mechanism & Impact |
| 1. Langflow Unauthorized Code Injection (CVE-2025-3248) | Critical (9.8) | Network | None Required | Mechanism: Unsafe code validation in an API endpoint allows arbitrary code execution via Python decorators. Impact: Compromise of AI application infrastructure and enterprise data pipelines. Actively exploited. |
| 2. Microsoft SharePoint Server RCE Chain (CVE-2025-53770, 53771) | Critical (9.8) | Network | None Required | Mechanism: Multi-stage attack bypassing authentication and exploiting unsafe deserialization. Impact: Full system control, data theft, and lateral movement. Confirmed active exploitation against government/finance sectors. |
| 3. Sudo Improper External Resource Reference (CVE-2025-32463) | High (7.8-9.3) | Local | Low-Privileged User | Mechanism: Race condition in sudo with --chroot allows loading malicious shared libraries.Impact: Local privilege escalation to root. Affects a vast number of Linux/Unix systems globally. |
| 4. Docker Desktop Inadequate Access Control (CVE-2025-9074) | Critical (7.8-9.3) | Local | None Required | Mechanism: Unauthenticated Docker Engine API exposure to containers via a hardcoded subnet. Impact: Container escape, host system compromise (Windows), and control of Docker infrastructure. |
| 5. WhatsApp & Apple Image I/O Exploit Chain (CVE-2025-55177, 43300) | Critical (10.0) | Network (Zero-Click) | None Required | Mechanism: WhatsApp auth bypass combined with Apple Image I/O out-of-bounds write via malicious images. Impact: Zero-click remote code execution on iOS/macOS. Used in targeted spyware attacks against journalists. |
| 6. SGLang Large Model Inference Framework RCE (CVE-2025-10164) | High (7.3) | Network | None Required | Mechanism: Unsafe deserialization of untrusted data in a model weights update endpoint. Impact: Remote code execution on GPU servers, potentially compromising AI model IP and inference infrastructure. |
| 7. Unitree Robot BLE Vulnerabilities (CVE-2025-35027, 60250, 60251) | High (7.3-8.2) | Adjacent (Bluetooth) | Limited Required | Mechanism: BLE command injection via static keys and hardcoded credentials. Impact: Root-level control of robots. Potential for “viral” propagation in robot swarms. |
| 8. FortiWeb Remote Code Execution Chain (CVE-2025-64446, 58034) | Critical (9.8) | Network | None Required | Mechanism: Authentication bypass via path traversal to legacy CGI interfaces, followed by RCE. Impact: Full control of WAF devices, enabling network pivot, traffic interception, and defense disablement. Actively exploited. |
| 9. Samsung Mobile Device Quram Library RCE (CVE-2025-21042) | High (8.8) | Network (Messaging) | None Required | Mechanism: Out-of-bounds write in image processing library triggered by malicious DNG files. Impact: Remote code execution used to deliver LANDFALL spyware for comprehensive device surveillance. |
| 10. React Server Components Code Injection (CVE-2025-55182) | Critical (10.0) | Network | None Required | Mechanism: Unsafe payload deserialization leading to prototype pollution and RCE. Impact: Pre-authentication RCE affecting major web frameworks like Next.js. Requires only a single HTTP request. |
1. Langflow Unauthorized Code Injection Vulnerability (CVE-2025-3248)
Severity: Critical | CVSS Score: 9.8 | Attack Vector: Network | Authentication: None Required
The Langflow vulnerability represents a critical flaw in one of the most popular open-source AI orchestration platforms, with over 79,000 GitHub stars signifying widespread adoption across enterprise environments.
CVE-2025-3248 stems from unsafe code validation logic in the unauthenticated /api/v1/validate/code endpoint, enabling remote attackers to execute arbitrary code without any authentication or authorization checks.
The vulnerability’s exploitation mechanism is particularly insidious, leveraging Python’s decorator evaluation behavior.
Attackers can embed malicious payloads inside decorators, triggering code execution during the parsing phase rather than during function execution.
When Langflow processes user-submitted code through Python’s ast.parse(), compile(), and exec() functions, the decorator expression is evaluated immediately, allowing attackers to achieve remote code execution before the code ever runs.
This technique bypasses traditional sandbox protections and input validation mechanisms designed to identify malicious intent at runtime.
The practical exploitation path is straightforward: an attacker sends a crafted HTTP POST request to the vulnerable endpoint with a specially constructed Python payload embedded in a decorator.
The payload executes with the privileges of the Langflow process, potentially compromising the entire AI application infrastructure, enterprise data pipelines, and connected systems.
Given Langflow’s role in building AI-powered agents and workflows for financial services, healthcare, and technology sectors, compromise of a vulnerable instance represents a critical risk to organizational operations.
Exploitation evidence emerged early, with CVE-2025-3248 added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on May 5, 2025, indicating active weaponization in threat actor arsenals.
The vulnerability affects all versions prior to 1.3.0, creating a wide window of exposure for organizations that have not actively maintained their deployment versions.
2. Microsoft SharePoint Server RCE Exploit Chain (CVE-2025-53770, CVE-2025-53771)
Severity: Critical | CVSS Score: 9.8 | Attack Vector: Network | Authentication: None Required
The SharePoint vulnerability chain, internally dubbed “ToolShell,” is among the most dangerous enterprise attacks discovered in 2025.
CVE-2025-53770 constitutes a critical unauthenticated remote code execution flaw affecting on-premises Microsoft SharePoint Server 2016, 2019, and Subscription Edition.
On July 19-20, 2025, Microsoft and CISA confirmed active exploitation of this vulnerability, with confirmed victims including government agencies and financial institutions.
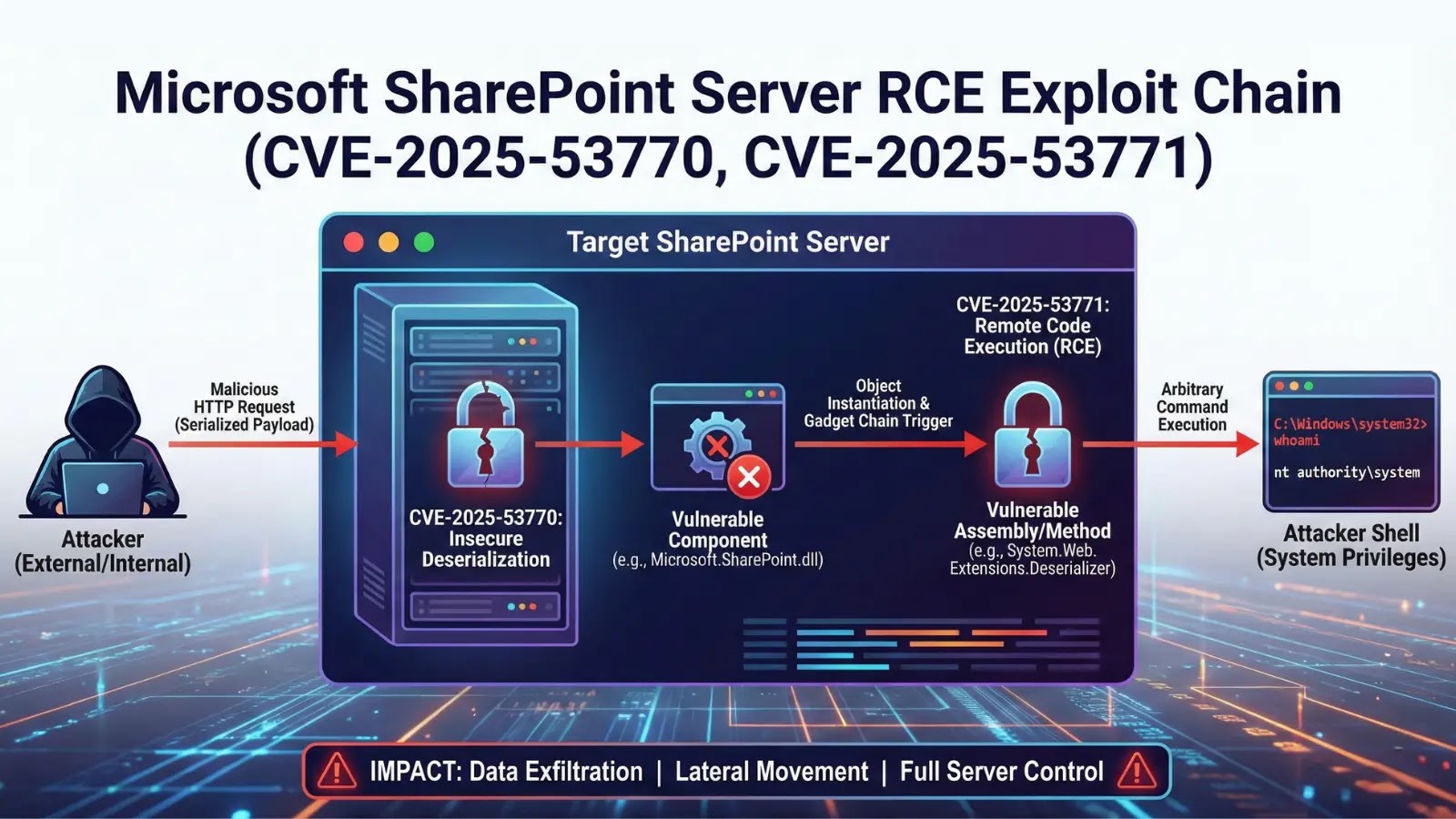
The exploitation chain operates through a three-stage process that systematically dismantles SharePoint’s security architecture.
First, attackers bypass authentication through crafted HTTP POST requests to the legacy WebPart editor endpoint (/_layouts/15/ToolPane.aspx?DisplayMode=Edit).
By setting a forged Referer header pointing to the SignOut endpoint, attackers trick SharePoint into processing unauthenticated requests as legitimate, internal system calls.
This authentication bypass exploits a trust relationship between SharePoint endpoints that was intended for internal workflows but can be abused remotely.
In the second stage, once authenticated access is achieved, attackers deploy a malicious .aspx file (typically named spinstall0.aspx) to the SharePoint layouts directory.
This file does not function as a traditional webshell; instead, it extracts cryptographic secrets from the server’s configuration, including the ValidationKey and DecryptionKey used by ASP.NET to sign and decrypt ViewState payloads.
These keys are fundamental to SharePoint’s deserialization security model.
The final stage leverages the stolen cryptographic material to craft valid, signed __VIEWSTATE tokens containing malicious payloads.
When these tokens are submitted to another SharePoint endpoint via GET request, the server deserializes them without additional validation, executing arbitrary code with the privileges of the application pool identity (typically NT AUTHORITY\IUSR).
This approach exploits unsafe deserialization of untrusted data a flaw that has plagued .NET applications for years.
The vulnerability’s impact extends beyond individual compromises. Attackers can execute PowerShell commands, access sensitive document libraries, create new administrative accounts, harvest credentials, and pivot laterally into connected systems.
Microsoft confirmed that CVE-2025-53770 and CVE-2025-53771 are related to two prior vulnerabilities (CVE-2025-49704 and CVE-2025-49706) disclosed at Pwn2Own Berlin, with the newer vulnerabilities providing “more robust protections” than the interim patches.
The continued discovery of variants in this attack family underscores the systematic nature of the underlying design flaw.
3. Sudo Improper External Resource Reference Vulnerability (CVE-2025-32463)
Severity: High | CVSS Score: 7.8-9.3 | Attack Vector: Local | Authentication: Low-Privileged User Required
CVE-2025-32463 is a critical privilege-escalation vulnerability in sudo, the fundamental Unix access-control utility present on virtually every Linux and Unix system worldwide.
Disclosed on June 30, 2025, by Stratascale Cyber Research Unit, this vulnerability allows local low-privileged users to escalate to root privileges by manipulating configuration files when using the --chroot (-R) option.
The vulnerability’s root cause originates from a change introduced in sudo version 1.9.14, where path resolution began occurring within the chroot environment before the sudoers file is evaluated.
This timing issue creates a race condition that attackers can exploit by inserting malicious configuration files into their controlled directory.
When a user runs sudo with the -R option into an attacker-controlled environment, sudo reads the malicious nsswitch.conf configuration file first.
This file can instruct the system to load a custom shared library (woot1337.so.2) crafted by the attacker. The exploit technique is remarkably straightforward, requiring only basic C programming skills.
An attacker creates a malicious shared library with a constructor function that immediately executes when the library is loaded.
The constructor calls setreuid(0,0) and setregid(0,0) to gain root privileges, then spawns a root-level bash shell.
Once the malicious library loads, the attacker instantly obtains complete system control without needing to exploit any subsequent vulnerabilities or race conditions.
The vulnerability affects sudo versions 1.9.14–1.9.17 (stable branch) and impacts a smaller but still significant 1.8.8–1.8.32 (legacy branch).
Organizations running any of these versions face critical risk, as the exploit requires only local access and low privileges a typical scenario following successful phishing, compromised credentials, or insider threats.
The practical exploitation timeline is compressed significantly: from initial compromise with low privileges to complete system control in minutes.
CVE-2025-32463 was added to CISA’s KEV catalog in July 2025, with Canada’s Cyber Centre and numerous national CERT agencies issuing emergency advisories.
The vulnerability impacts critical infrastructure, cloud environments, and enterprise systems globally, making it a top priority for patch management teams.
4. Docker Desktop Inadequate Access Control Vulnerability (CVE-2025-9074)
Severity: Critical | CVSS Score: 7.8-9.3 | Attack Vector: Local | Authentication: None Required
CVE-2025-9074 exposes a fundamental access control failure in Docker Desktop, affecting both Windows and macOS versions prior to 4.44.3.
The vulnerability allows locally running Linux containers to access the Docker Engine API at the hardcoded subnet address 192.168.65.7:2375 without any authentication, regardless of Enhanced Container Isolation (ECI) settings.
Docker Desktop implements a networking bridge between host systems and Linux containers, using a virtual subnet for internal communication.
The vulnerability arises because Docker Desktop exposes its engine API on this subnet without implementing network-level authentication or encryption.
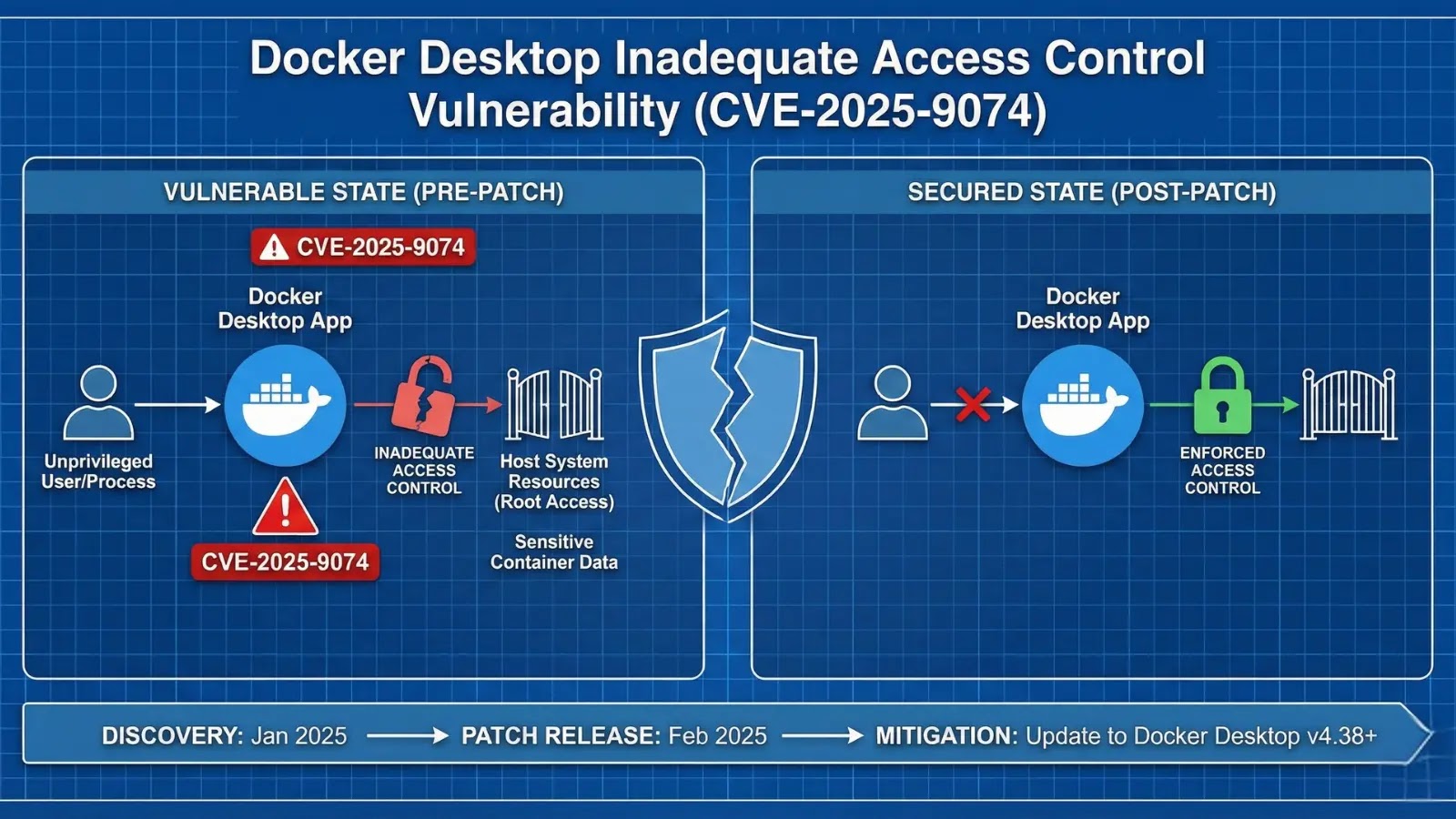
A malicious container, whether launched by a user or deployed through a supply chain attack, can make unauthenticated requests to the Docker Engine API and execute arbitrary commands with full engine privileges.
The exploitation vector expands significantly depending on the host operating system.
On Docker Desktop for Windows using WSL2 backend, attackers can mount the host’s filesystem with administrative privileges equivalent to the Docker Desktop user, read sensitive files, and install persistent malware by modifying system DLLs.
On macOS, while isolated by the application sandbox, attackers can backdoor the Docker application itself and gain control over all containers and images.
In both scenarios, the attacker escalates from a compromised container to controlling the entire Docker infrastructure.
The practical impact manifests across multiple attack scenarios.
First, supply chain attacks can inject malicious containers into enterprise registries when deployed in Docker Desktop environments. These containers achieve immediate Docker Engine access and compromise the development workstation.
Second, vulnerable development workstations become pivotal for lateral movement, as Docker Desktop is often run with elevated privileges and contains credentials for production registries and orchestration platforms.
Third, the vulnerability enables rapid containerized botnet creation, where compromised nodes commandeer additional containers to form distributed attack infrastructure.
Docker addressed CVE-2025-9074 in version 4.44.3, implementing authentication requirements for Docker Engine API access from containers.
However, the wide deployment of Docker Desktop across development teams, with auto-update frequently disabled, has created a substantial installed base of vulnerable systems.
5. Combined Exploit Chain: WhatsApp Authorization Validation Vulnerability and Apple Image I/O Out-of-Bounds Write (CVE-2025-55177, CVE-2025-43300)
Severity: Critical | CVSS Score: 10.0 (Combined) | Attack Vector: Network (WhatsApp), Zero-Click | Authentication: None Required
The chained vulnerability combining CVE-2025-55177 in WhatsApp with CVE-2025-43300 in Apple’s ImageIO framework represents one of 2025’s most sophisticated attack chains, targeting journalists and human rights defenders with state-sponsored spyware.
This exploit chain operationalizes a zero-click attack methodology, requiring no user interaction whatsoever to compromise iOS and macOS devices.
CVE-2025-55177 stems from incomplete authorization checks in WhatsApp’s linked device synchronization messages.
WhatsApp allows users to link secondary devices through a synchronization process; however, the authorization validation fails to properly verify that synchronization messages originate from legitimate linked devices.
This authorization bypass enables remote attackers to force arbitrary content processing on target devices by triggering malicious synchronization messages containing URLs pointing to attacker-controlled servers.
CVE-2025-43300 represents an out-of-bounds write vulnerability in Apple’s Image I/O framework, which handles image processing across iOS, iPadOS, and macOS.
The vulnerability exists in the parsing logic for DNG (Digital Negative) and JPEG Lossless image formats.
A validation gap between TIFF metadata and embedded JPEG streams causes the parser to allocate buffers based on SamplesPerPixel metadata, while the JPEG decoder later uses a different component count from the image stream.
When these values conflict, more pixel data is written than the buffer was sized for, resulting in a classic out-of-bounds write vulnerability.
The attack chain operates as follows: An attacker sends a synchronization message via WhatsApp, exploiting CVE-2025-55177, forcing the target device to process a malicious DNG image file from a remote URL.
As the device processes the image, Image I/O invokes vulnerable code paths, writing beyond allocated memory boundaries.
This memory corruption enables arbitrary code execution within the Image I/O process, which operates with high privileges for media processing.
Second-stage payloads can then establish persistence and coordinate surveillance functionality.
The sophistication lies in the coordinated deployment: WhatsApp’s authorization bypass provides zero-click delivery, while the Image I/O vulnerability provides reliable code execution.
Combined, these create a complete exploitation chain requiring zero user interaction.
WhatsApp confirmed that approximately 200 individuals, primarily journalists and human rights defenders in the Middle East, were targeted over a three-month period.
Apple rushed emergency patches in August 2025, and WhatsApp released updates shortly thereafter, but the incident underscores the systematic nature of nation-state surveillance operations targeting vulnerable populations.
6. SGLang Large Model Inference Framework Remote Code Execution (CVE-2025-10164)
Severity: High | CVSS Score: 7.3 | Attack Vector: Network | Authentication: None Required
CVE-2025-10164 represents a critical vulnerability in SGLang, an increasingly popular large language model inference framework used to serve AI models in production environments.
The vulnerability arises from unsafe deserialization of untrusted data in the /update_weights_from_tensor endpoint, allowing remote code execution on GPU servers running vulnerable versions.
Machine learning inference frameworks like SGLang must efficiently transfer serialized tensor data (mathematical arrays) between clients and servers, particularly when distributing computations across GPU clusters.
However, deserialization of untrusted serialized objects represents a well-known vulnerability pattern in Python applications.
SGLang’s implementation fails to implement adequate validation before deserializing the serialized_named_tensors parameter, allowing attackers to inject malicious payloads that execute arbitrary code during deserialization.
The practical impact extends beyond individual compromised servers. Production AI inference clusters typically contain thousands of nodes running identical vulnerable versions of SGLang.
A single compromised node becomes a pivot point for lateral movement across the entire cluster, enabling attackers to control distributed model serving infrastructure.
This infrastructure often contains valuable intellectual property (trained model weights), customer data for inference, and credentials for connecting to upstream systems.
The vulnerability gained attention within the AI security community due to the rapid response from SGLang maintainers and collaborative coordination with potential victims to prevent widespread in-the-wild exploitation.
This proactive incident response prevented the vulnerability from being weaponized at scale, highlighting how rapid disclosure and coordinated patching can mitigate zero-day risk even for emerging technologies.
7. Unitree Robot BLE Vulnerabilities (CVE-2025-35027, CVE-2025-60250, CVE-2025-60251)
Severity: High | CVSS Score: 7.3-8.2 | Attack Vector: Adjacent (Bluetooth) | Authentication: Limited Required
CVE-2025-35027 represents a critical command injection vulnerability in multiple robotic products from Unitree, including the popular Go2 (quadruped) and G1 (humanoid) robot lines.
The vulnerability allows attackers to achieve root-level command execution on affected robots through the Bluetooth Low Energy (BLE) interface, creating risks for physical systems and critical infrastructure applications.
Unitree robots intentionally expose a WiFi configuration interface over BLE to allow users to configure network connectivity without physical access.
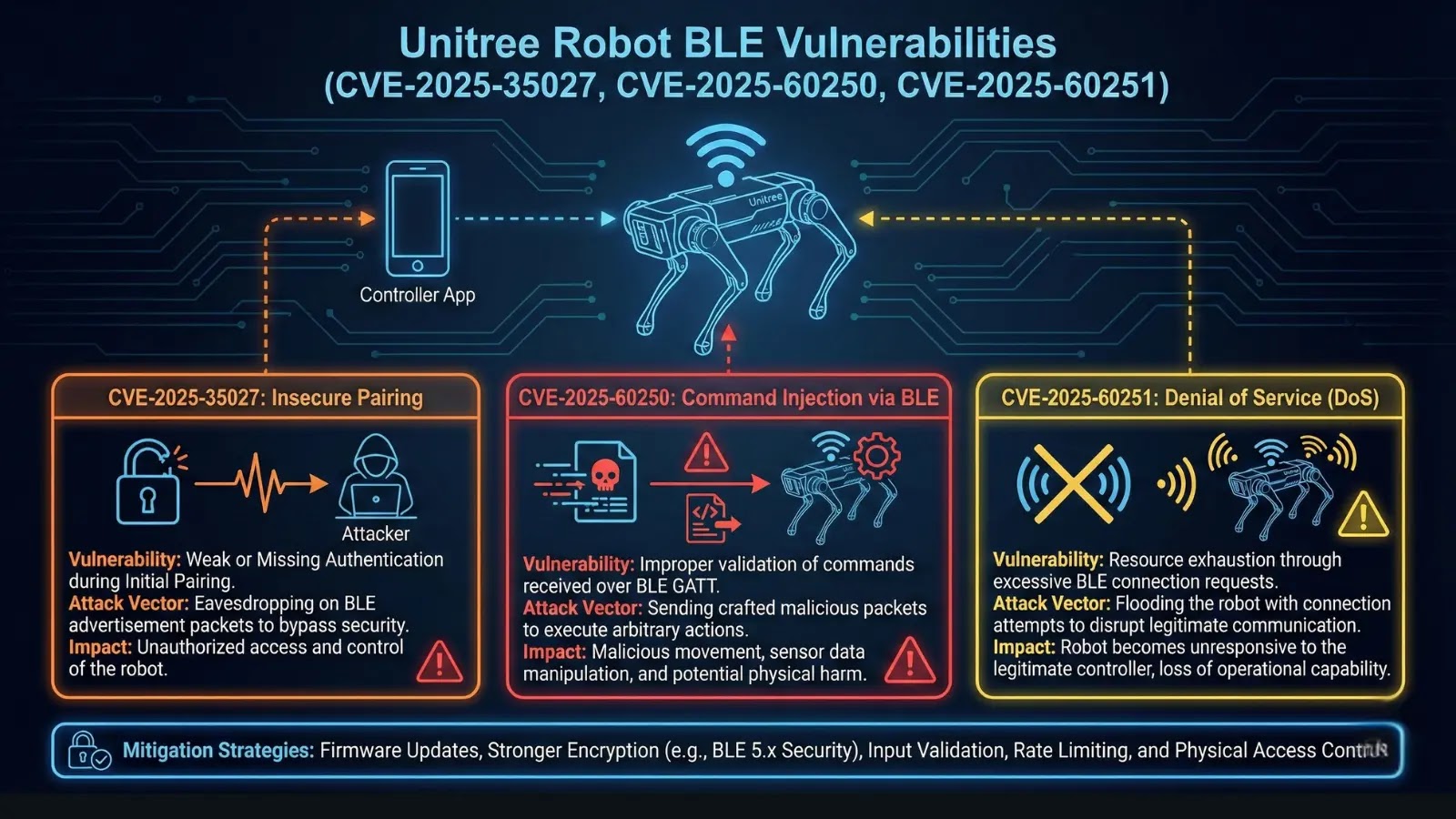
The vulnerability chain combines three distinct flaws: CVE-2025-60250 (static encryption key in BLE), CVE-2025-60251 (hardcoded authentication string), and CVE-2025-35027 (command injection).
An attacker can pair with the robot using the static AES key and IV, then authenticate using the hardcoded “unitree” string.
Once authenticated, the attacker can supply malicious WiFi SSID or password strings containing shell metacharacters (pipe, semicolon, command substitution syntax).
These values are passed directly to the wpa_supplicant_restart.sh script via sudo, executed with root privileges.
An attacker can immediately gain root shell access or inject arbitrary commands for persistence, data exfiltration, or physical system compromise.
In scenarios where multiple robots operate in proximity (swarms, warehouse deployments, research facilities), a single compromised robot can propagate the attack to neighboring robots through automated exploitation.
The disclosure noted that a robot under attacker control can move toward other robots and compromise them automatically a “viral” propagation pattern.
Applications of these robots in security-sensitive environments (bomb defusal, hostage rescue, critical infrastructure inspection) create elevated risk profiles where device compromise could endanger lives.
As of September 2025, all Unitree Go2, G1, H1, and B2 devices with current firmware versions remain vulnerable, with the vendor indicating fixes may require years to implement.
8. FortiWeb Remote Code Execution Vulnerability Chain (CVE-2025-64446, CVE-2025-58034)
Severity: Critical | CVSS Score: 9.8 | Attack Vector: Network | Authentication: None Required
CVE-2025-64446 represents a critical authentication bypass vulnerability in Fortinet FortiWeb web application firewalls, affecting multiple versions and actively exploited since early October 2025.
The vulnerability combines two design flaws: relative path traversal (CWE-23) and authentication bypass via alternate path (CWE-288), enabling unauthenticated attackers to create administrative accounts and gain complete control over vulnerable devices.
FortiWeb implements a modern REST API for administrative management, which is supposed to require authentication for all operations.
However, legacy CGI-based administrative interfaces remain present in the system for backward compatibility.
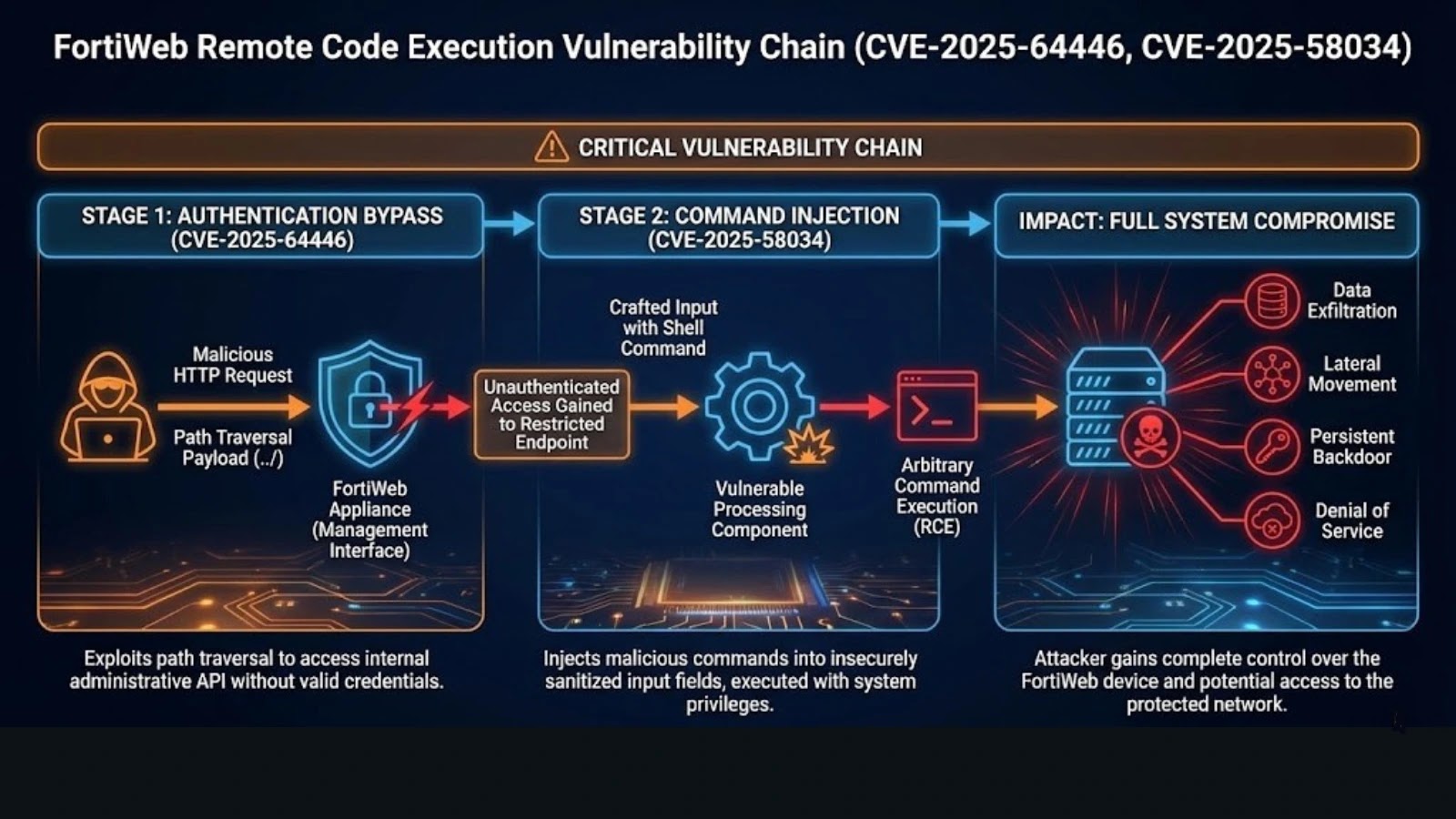
An attacker can craft an HTTP POST request to /api/v2.0/cmdb/system/admin with specific URL encoding that routes the request through the REST API’s path traversal logic to the unprotected CGI processor.
The CGI processor relies on an HTTP header (CGIINFO) for authentication rather than standard HTTP authentication mechanisms, creating a bypass condition.
By sending a specially crafted POST request with the correct CGIINFO header value, attackers bypass all authentication checks and directly invoke the CGI script responsible for user creation.
The attacker can immediately create a new administrator account with full privileges, then use those credentials to access the management interface and reconfigure the WAF to facilitate further attacks.
FortiWeb devices operate as critical security infrastructure, often placed directly at network boundaries protecting web applications and APIs.
A compromised FortiWeb instance becomes a powerful pivot point for internal network access, as attackers can disable security rules, create traffic forwarding, harvest credentials transiting through the WAF, and maintain persistent backdoors.
The vulnerability’s severity prompted CISA to add CVE-2025-64446 to its KEV catalog with a mandatory remediation deadline of November 21, 2025.
Exploitation evidence emerged in public disclosures from security research organizations, and watchToR published Python-based proof-of-concept code demonstrating reliable exploitation.
The combination of widespread internet exposure of FortiWeb devices (for remote access and DDoS protection) with the unauthenticated nature of the vulnerability created a significant attack surface.
9. Samsung Mobile Device Quram Image Parsing Library Remote Code Execution (CVE-2025-21042)
Severity: High | CVSS Score: 8.8 | Attack Vector: Network (via Messaging Apps) | Authentication: None Required
CVE-2025-21042 represents a critical out-of-bounds write vulnerability in Samsung’s libimagecodec.quram.so image processing library, used by millions of older Samsung Galaxy devices running Android versions 13-16.
The vulnerability was actively exploited in the wild to deliver the LANDFALL spyware malware targeting individuals in the Middle East.
Samsung’s Quram image processing library handles DNG (Digital Negative) format images, a lossless raw image format commonly used by professional photographers.
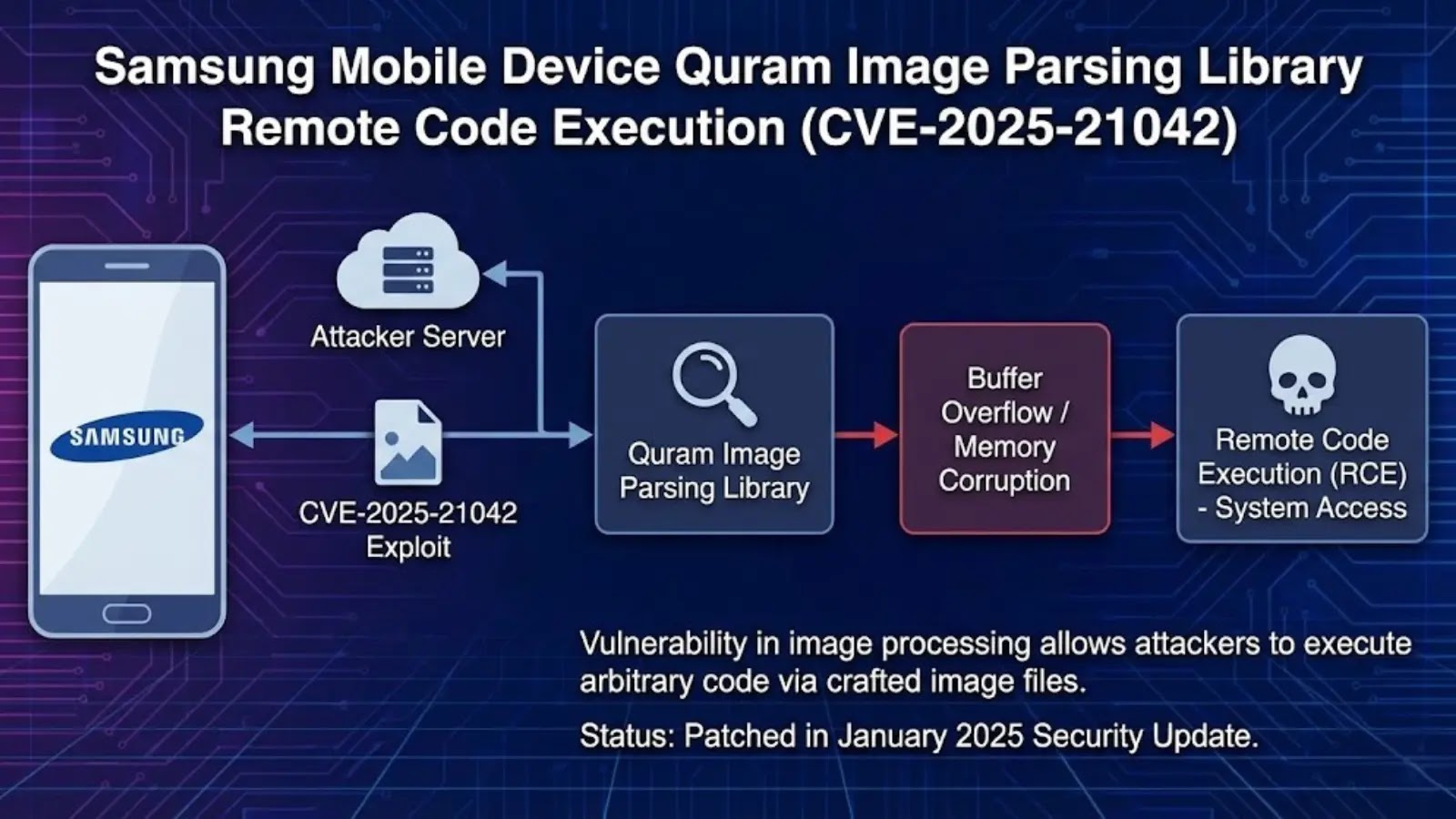
A malicious DNG file with carefully crafted image headers can trigger an out-of-bounds write condition in the library’s parsing code, leading to memory corruption and arbitrary code execution.
Researchers discovered that attackers embedded malicious DNG files within ZIP archives, then appended these archives to DNG files for delivery via messaging applications like WhatsApp.
The LANDFALL spyware campaign leveraged this vulnerability to deliver a two-stage attack: a loader component (b.so) establishing backdoor functionality, and a SELinux policy manipulator (l.so) designed to grant elevated permissions and persistence.
Once the DNG file is processed, potentially through automatic thumbnail generation or metadata extraction in messaging apps, the vulnerability triggers, executing the embedded malware without user interaction.
The practical impact on device security is severe. LANDFALL enabled comprehensive surveillance including microphone recording, location tracking, photo collection, contact harvesting, and call log exfiltration.
The vulnerability affects flagship Samsung Galaxy models (S22, S23, S24, Z Fold4, Z Flip4) that remain widely deployed in vulnerable configurations.
While Samsung patched the vulnerability in April 2025, the extended timeline of exploitation in the wild (spanning July 2024 through early 2025) indicates millions of devices remain at risk.
Android fragmentation the slow deployment of security patches across device models and carriers—creates a long tail of vulnerable devices in active use.
Unlike iOS where Apple controls the entire ecosystem, Android device fragmentation means many users remain vulnerable for extended periods post-disclosure.
10. React Server Components Code Injection Vulnerability (CVE-2025-55182)
Severity: Critical | CVSS Score: 10.0 | Attack Vector: Network | Authentication: None Required
CVE-2025-55182 represents a critical pre-authentication remote code execution vulnerability in React Server Components, disclosed on December 3, 2025.
The vulnerability achieves the maximum CVSS score of 10.0 due to its complete lack of authentication requirements and its impact on widely deployed modern web frameworks, including Next.js, React Router, and various Vite/Parcel implementations.
React Server Components represent an emerging paradigm in web development, allowing server-side logic to be composed with client-side components without explicit API definitions.
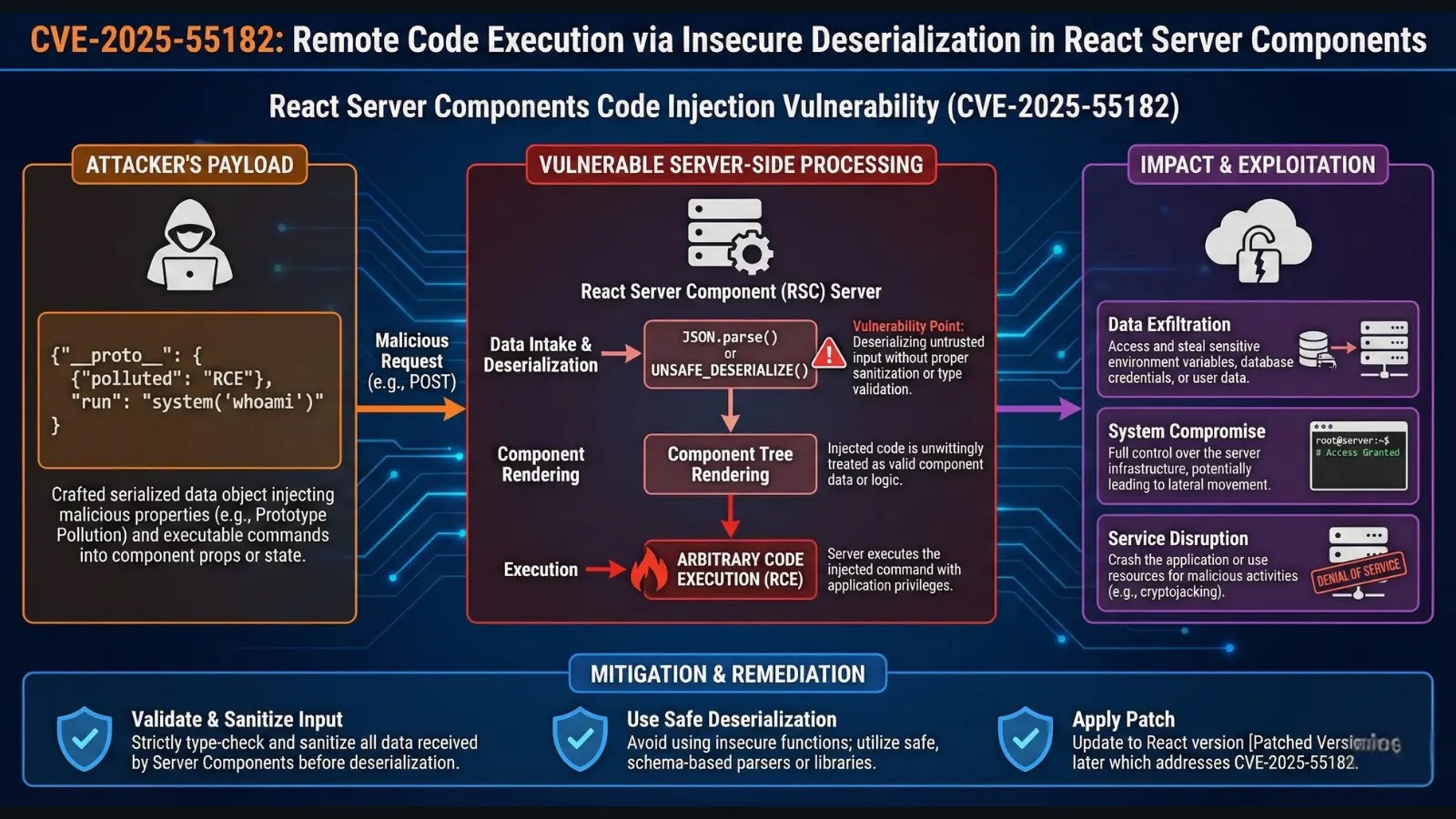
However, this convenience introduces security complexity. The vulnerability exists in how React Server Components handle payload deserialization on HTTP requests targeting Server Function endpoints.
When processing incoming requests, React deserializes payloads without adequate validation, creating a direct pathway for attackers to execute arbitrary code.
The vulnerability exploits prototype pollution in JavaScript’s prototype chain. An attacker crafts a specially structured JSON payload that, when deserialized, pollutes the prototype of JavaScript objects.
By referencing native Node.js functions like child_process.execSync, attackers can escalate prototype pollution to direct code execution with server-side privileges.
The attack requires only a single HTTP POST request to a Server Function endpoint no authentication, no complex exploit chains, no user interaction necessary.
Affected packages include react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack in versions 19.0.0 through 19.2.0.
Critically, major frameworks built on React Server Components are also impacted, including Next.js (versions 15.x and 16.x), React Router with RSC APIs, Expo, Redwood SDK, and Waku.
Given that Next.js is one of the most popular React frameworks for production deployments, the vulnerability affects a substantial portion of modern web infrastructure.
The exploit timeline demonstrates the urgency of patching. Within hours of disclosure, multiple researchers published proof-of-concept code demonstrating reliable exploitation.
Attack demonstrations showed the vulnerability enables reading arbitrary files, establishing persistent reverse shells, and accessing environment variables containing database credentials and API keys.
MongoBleed Vulnerability (CVE-2025-14847)
MongoBleed arises from improper handling of length parameters in zlib-compressed MongoDB wire protocol messages, causing the server to return uninitialized heap memory alongside valid responses. Attackers send crafted, undersized compressed packets remotely without authentication, triggering a buffer over-read that leaks adjacent memory contents.
Leaked memory often contains high-value secrets like plaintext credentials, API keys, AWS tokens, and session data from concurrent connections, enabling credential stuffing or lateral movement. Exploitation requires network access and zlib compression enabled (default in many deployments), with public PoCs automating repeated probes for sensitive fragments.
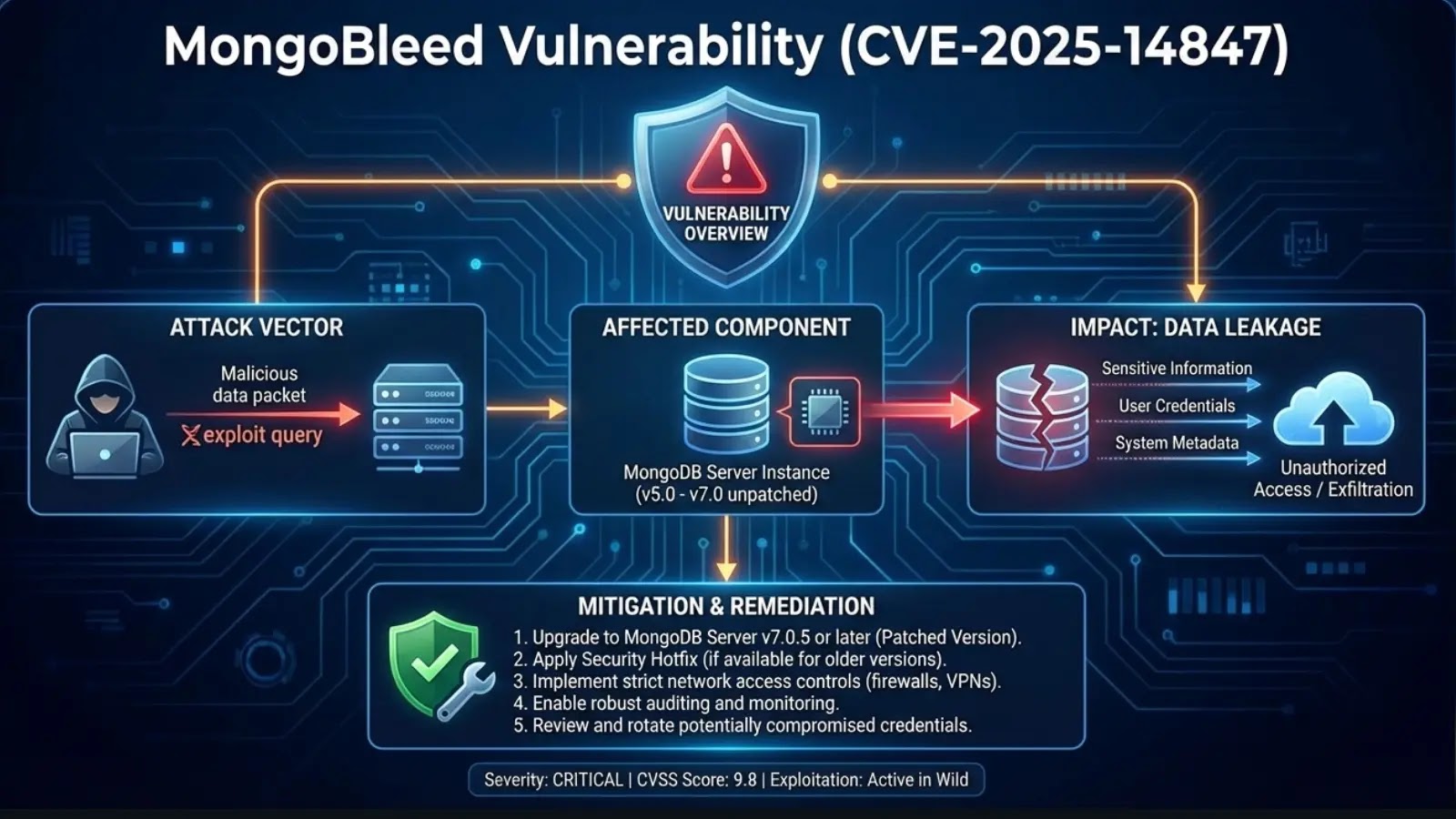
Discovered internally by MongoDB on December 12, 2025, patches rolled out rapidly: Atlas fleet auto-updated by December 18, community/enterprise builds available December 19. CISA added it to the KEV catalog on December 29, confirming wild exploitation against ~87,000 exposed instances, concentrated in the US, China, and Germany.
The ten vulnerabilities examined in this analysis represent the most critical risks facing enterprises, cloud infrastructure, mobile devices, and IoT systems in 2025.
These vulnerabilities share common characteristics: they enable unauthenticated remote code execution or privilege escalation, they affect widely deployed software across multiple sectors, and they are actively being exploited by sophisticated threat actors including nation-state APT groups and ransomware operators.
The broader vulnerability landscape reflects an alarming acceleration in attack sophistication and speed. Over 21,500 CVEs were disclosed in H1 2025 alone, with approximately 38% rated as High or Critical severity.
More critically, VulnCheck identified 432 CVEs with evidence of in-the-wild exploitation in the first half of 2025, with 32.1% exploited on or before the disclosure date, indicating widespread zero-day weaponization.
These statistics demonstrate that vulnerability management has fundamentally changed: defenders cannot simply defer patching to convenient maintenance windows, as attackers are weaponizing flaws within hours of disclosure.
Nation-state threat actors continue leading the charge, targeting enterprise security infrastructure, government systems, and critical infrastructure with sophisticated exploit chains.
The pivot toward targeting enterprise security products (VPNs, firewalls, WAFs) reflects a strategic shift where attackers prioritize compromising the protective infrastructure that guards corporate networks, enabling lateral movement at scale.
This trend, alongside increasing exploitation of AI/ML frameworks and emerging technologies, suggests that organizations must expand vulnerability management beyond traditional enterprise software to include emerging technologies, infrastructure components, and supply chain dependencies.
Immediate actions include prioritizing patches for all ten vulnerabilities examined here, implementing compensating controls where immediate patching is not feasible, and establishing continuous vulnerability intelligence programs that monitor CISA’s KEV Catalog and vendor advisories in real time.
The 2025 vulnerability landscape validates that the traditional reactive approach to patching is no longer viable. Organizations that have not shifted to proactive, continuous vulnerability management face existential risk from rapid exploitation cycles.












