A sophisticated cyberattack targeting Oracle E-Business Suite (EBS) customers has exposed critical vulnerabilities in enterprise resource planning systems, compromising an estimated 100 organizations worldwide between July and October 2025.
The campaign, attributed to the notorious Clop ransomware group and linked to the financially motivated threat actor FIN11, exploited a zero-day vulnerability, CVE-2025-61882, to achieve unauthenticated remote code execution on internet-facing EBS portals.
With nearly 30 victims publicly named and data leaks containing hundreds of gigabytes to several terabytes of sensitive corporate information, this incident serves as a stark reminder of the evolving threat landscape facing modern enterprises.
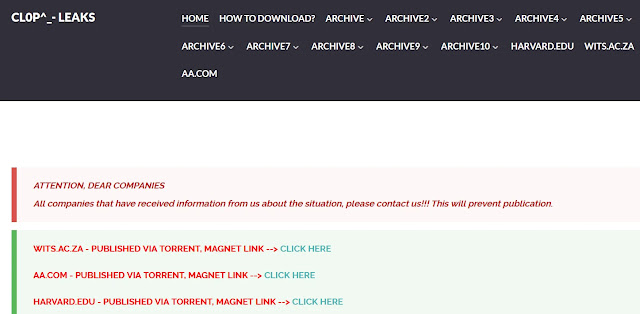
The breach affected prominent organizations, including Harvard University, The Washington Post, Logitech, Schneider Electric, and American Airlines’ subsidiary Envoy Air, exposing financial records, human resources data, supply chain information, and customer details.
The Oracle EBS campaign represents a textbook example of how threat actors exploit widely used enterprise software to achieve mass compromise.
Oracle E-Business Suite serves as the operational backbone for thousands of organizations worldwide, managing critical functions including finance, human resources, supply chain operations, procurement, and customer relationship management.
By compromising this centralized platform, attackers gained access to the most sensitive data repositories within victim organizations, effectively turning a trusted business tool into an attack vector.
Google Threat Intelligence Group (GTIG) and Mandiant researchers traced the earliest exploitation activity to July 10, 2025, with confirmed data theft beginning by August 9, 2025, weeks before Oracle released emergency patches.
The sophisticated nature of the attack, involving fileless malware and multi-stage payloads, enabled the threat actors to evade traditional file-based detection systems while maintaining persistent access to compromised environments.
Charles Carmakal, CTO of Mandiant Consulting, emphasized the pre-patch exploitation timeline, noting that attackers leveraged the zero-day vulnerability before defensive measures became available.
The campaign surfaced publicly on September 29, 2025, when executives at numerous organizations received extortion emails from actors claiming affiliation with the Clop brand.
These emails, sent from hundreds of compromised third-party accounts to bypass spam filters, alleged the theft of sensitive data from victims’ Oracle EBS environments and threatened public disclosure unless ransom demands were met.
The use of stolen credentials from infostealer malware logs represents a sophisticated social engineering tactic designed to add legitimacy to the extortion attempts.
Technical Exploitation: A Five-Stage Attack Chain
CVE-2025-61882, assigned a critical CVSS score of 9.8, enabled unauthenticated attackers to achieve remote code execution on Oracle EBS versions 12.2.3 through 12.2.14 without requiring any user interaction.
The vulnerability resides in the Oracle Concurrent Processing component and was actively exploited in the wild before patches became available, qualifying it as a true zero-day threat.
Security researchers from watchTowr Labs published a comprehensive technical analysis revealing that the exploit chains together five distinct vulnerabilities to achieve pre-authenticated remote code execution.
The attack begins with a Server-Side Request Forgery (SSRF) vulnerability in the /OA_HTML/configurator/UiServlet endpoint, which accepts XML documents from unauthenticated users via the getUiType parameter.
When the redirectFromJsp parameter is present, the servlet parses the XML to extract a return_url and creates an outbound HTTP request, allowing attackers to force the server to contact arbitrary hosts.
With SSRF control established, attackers inject Carriage-Return Line-Feed (CRLF) sequences into the URL payload to manipulate request framing and insert malicious headers.
This CRLF injection enables adversaries to convert simple GET requests into crafted POST requests and smuggle additional data to downstream services. The exploit leverages HTTP connection reuse through keep-alive mechanisms, allowing staged requests to be pipelined over the same TCP socket for improved timing reliability.
Armed with POST-capable SSRF and header injection, attackers target internal services that are normally unreachable from public interfaces. Oracle EBS installations frequently expose internal HTTP services bound to private IP addresses and ports, commonly on port 7201.
The exploit uses path-traversal techniques to bypass pathname-based authentication filters and retrieve restricted JSP pages, transforming internal-only resources into attacker-controllable execution paths. Researchers documented this technique by accessing the ieshostedsurvey.jsp endpoint via path manipulation: /OA_HTML/help/../ieshostedsurvey.jsp.
Once attackers reach the vulnerable JSP endpoint, the application constructs an XSL stylesheet URL by concatenating the incoming Host header with /ieshostedsurvey.xsl.
The server creates a URL object and passes it to Java’s XSL processing pipeline, which downloads and executes the stylesheet from the attacker-controlled server.
Because Java XSLT supports extension functions and can invoke arbitrary Java classes, the attacker-supplied XSL file decodes payloads and invokes javax.script other extensions to execute arbitrary code within the Java Virtual Machine.
This final unsafe XSLT processing stage grants attackers complete remote code execution capability on the compromised system.
Mandiant investigators identified a secondary exploitation chain targeting the /OA_HTML/SyncServlet component in the August 2025 activity. This alternate attack path demonstrated the threat actors’ sophisticated understanding of Oracle EBS architecture and their ability to develop multiple exploitation techniques.
The malware deployed following exploitation included GOLDVEIN.JAVA, an in-memory Java-based loader that fetches second-stage payloads, showing logical similarities to malware used in suspected Clop campaigns against Cleo managed file transfer systems in late 2024.
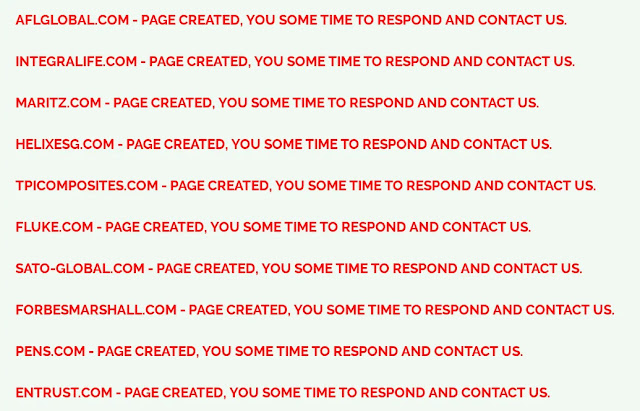
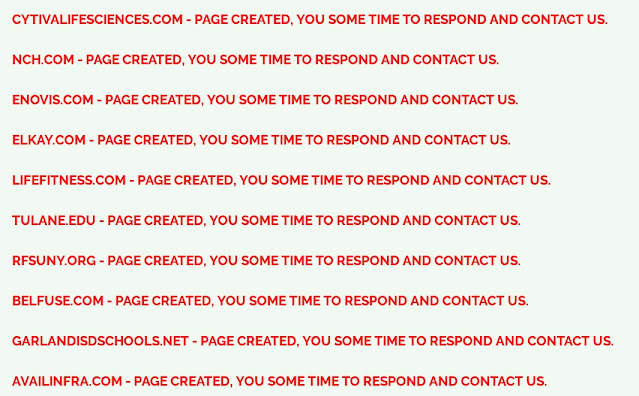
As of November 2025, the Clop data leak site listed 29 alleged victims spanning multiple sectors, including education, media, manufacturing, aerospace, technology, professional services, mining, construction, insurance, financial services, transportation, automotive, energy, and HVAC industries.
Confirmed victims who publicly acknowledged the breach include Harvard University, Wits University in South Africa, American Airlines subsidiary Envoy Air, The Washington Post, and Logitech.
Major industrial corporations named on the leak site include Schneider Electric, Emerson, Cox Enterprises, Pan American Silver, LKQ Corporation, and Copeland, though most have not publicly confirmed the incidents.
The Washington Post confirmed on November 6, 2025, that it was among the victims, though the organization declined to share specific details about the compromise. Logitech similarly disclosed a data breach shortly after being named on the Clop leak site.
In a particularly severe case, GlobalLogic reported on November 11, 2025, that personal information of 10,471 current and former employees was stolen, including names, addresses, phone numbers, emergency contacts, email addresses, dates of birth, nationalities, passport information, tax identifiers, salary information, and bank account details.
Cybercriminals leaked data allegedly stolen from 18 victims, with some releases totaling hundreds of gigabytes and others reaching several terabytes. Limited structural analysis conducted by security researchers concluded that the leaked files likely originated from Oracle environments, lending credibility to the threat actors’ claims.
The extent of data exposure underscores the comprehensive access attackers achieved to victims’ EBS systems, which integrate finance, HR, supply chain, and procurement functions into centralized databases.
Shadowserver researchers released data on October 8, 2025, showing 576 potentially vulnerable IP addresses based on internet scanning for the zero-day vulnerability.
This figure represents only internet-exposed Oracle EBS instances and does not account for organizations that may have been compromised but maintained the systems behind firewalls or other network security controls.
Threat Actor Attribution and Tactics
The campaign bears the hallmarks of the Clop ransomware group, also tracked as FIN11 and TA505, a financially motivated threat actor with a documented history of mass exploitation campaigns targeting enterprise software vulnerabilities.
To substantiate their extortion claims, threat actors provided legitimate file listings from victim EBS environments to multiple organizations, with data timestamps dating back to mid-August 2025.
This tactic demonstrates the attackers’ possession of genuine stolen data and serves to pressure victims into negotiating ransom payments. Consistent with modern extortion operations, the threat actors typically specify payment amounts and methods only after victims contact them and indicate authorization to negotiate.
The campaign methodology mirrors previous Clop operations, particularly the mass exploitation of vulnerabilities in MOVEit file transfer software in 2023, which affected hundreds of organizations globally.
The group was also linked to the exploitation of Cleo file transfer software flaws starting in late 2024 and previous attacks on Fortra file transfer products. This pattern of targeting widely deployed enterprise software to simultaneously compromise numerous organizations has become a signature tactic for the threat actor.
Mandiant researchers identified overlaps between the Oracle EBS campaign and a leaked exploit code posted on October 3, 2025, by Scattered Lapsus$ Hunters, also known as ShinyHunters, a group linked to social engineering attacks against retailers and other companies.
The group claimed credit for a recent attack disrupting production at Jaguar Land Rover. However, researchers emphasized they could not definitively assess whether the July exploitation activity involved that specific exploit code or establish direct connections between the early Oracle activity and ShinyHunters.
GTIG analysis noted that post-exploitation tooling showed “logical similarities” to malware deployed in other suspected Clop campaigns.
The use of compromised third-party email accounts for the extortion campaign represents a sophisticated operational security measure, as credentials sourced from infostealer malware logs on underground forums enable threat actors to send messages that bypass spam filters and appear more legitimate to recipients.
Oracle’s Response and Patch Timeline
Oracle’s response to the vulnerability disclosure followed a multi-stage timeline that raised concerns about the gap between initial exploitation and patch availability.
The company released a Critical Patch Update in July 2025 that addressed several EBS vulnerabilities, but this update predated the emergency patch for CVE-2025-61882 by several months. Security researchers documented suspicious activity potentially related to exploitation dating back to July 10, 2025, even before the July patches were released.
On October 2, 2025, Oracle reported that threat actors may have exploited vulnerabilities patched in the July 2025 update and recommended that customers apply the latest Critical Patch Updates.
Two days later, on October 4, 2025, Oracle released an emergency Security Alert specifically addressing CVE-2025-61882. The advisory confirmed that the vulnerability is remotely exploitable without authentication and, if successfully exploited, may result in remote code execution.
Oracle strongly recommends that customers apply the updates immediately, emphasizing its longstanding guidance to remain on actively supported versions and to apply all Security Alerts and Critical Patch Updates without delay.
The emergency patch carried a critical prerequisite: organizations must first install the October 2023 Critical Patch Update before applying the CVE-2025-61882 patch.
This requirement can complicate and delay remediation efforts for organizations that do not maintain current patch levels. Oracle updated the guidance on October 11, 2025, with GTIG assessing that Oracle EBS servers updated through this patch were likely no longer vulnerable to known exploitation chains.
On October 8, 2025, Oracle released an additional Security Alert for CVE-2025-61884, a high-severity vulnerability affecting the Runtime UI component of Oracle Configurator.
This vulnerability enables unauthenticated remote attackers with network access via HTTP to compromise Oracle Configurator and access sensitive resources. Rob Duhart, Oracle’s Chief Security Officer, noted that the vulnerability affects “some deployments” of Oracle E-Business Suite, suggesting configuration-dependent exposure.
Oracle’s advisories included Indicators of Compromise (IOCs) derived from observed exploitation, including IP addresses, command patterns, and file hashes for suspected exploit scripts.
The publication of these IOCs enabled defensive teams to hunt for evidence of compromise in their environments, though the fileless nature of the malware complicated detection efforts.
Zero-Day Exploitation Before Patches
The timeline between initial exploitation and patch availability represents one of the most concerning aspects of the Oracle EBS campaign. Mandiant confirmed that threat actors exploited CVE-2025-61882 as a zero-day vulnerability against Oracle EBS customers as early as August 9, 2025, with additional suspicious activity potentially dating back to July 10, 2025.
Oracle did not release the emergency patch until October 4, 2025, creating a window of approximately eight weeks between confirmed exploitation and patch availability, during which victims had no vendor-supplied defensive measures.
This exploitation timeline highlights a fundamental challenge in enterprise software security: the asymmetry between attacker capabilities and defender readiness.
Sophisticated threat actors invest significant resources in vulnerability research and exploit development, often discovering flaws before vendors or security researchers identify them.
Once weaponized, these zero-day vulnerabilities give attackers a critical advantage, enabling them to compromise systems before defenses are in place.
Charles Carmakal emphasized the gravity of the pre-patch exploitation timeline in his LinkedIn post, warning that organizations should proactively investigate for signs of compromise regardless of their current patching status.
This guidance recognizes that applying patches remediates future exploitation of vulnerabilities but does not address existing compromises that occurred during the zero-day window.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-61882 to its Known Exploited Vulnerabilities (KEV) catalog on October 6, 2025, confirming active exploitation in ransomware campaigns.
This designation triggers binding operational directive requirements for federal agencies to patch affected systems within specified timeframes and serves as a strong signal to private sector organizations about the critical nature of the threat.
Several security experts recommend migrating from on-premises Oracle EBS to cloud-based Oracle Fusion Cloud Applications to enhance security.
SaaS models like Oracle Fusion shift some security responsibilities to the vendor, who continuously updates security controls. The Oracle Fusion Cloud Supply Chain Management platform integrates security measures and supports decision-making during disruptions.
Organizations on EBS should adopt a “security-first mindset” from the design phase, embedding security into architecture, access controls, and patch management. Regular security assessments, including vulnerability scanning and penetration testing, help identify weaknesses before they can be exploited.
The Oracle EBS campaign affecting around 30 organizations highlights systemic challenges against sophisticated threats. The exploitation of zero-day vulnerabilities and fileless malware showcases modern cyber threats, indicating that organizations must limit internet exposure, maintain patch discipline, and implement defense-in-depth strategies.
The impact of this campaign may reach beyond the identified victims, with assessments suggesting over 100 organizations could be affected. Organizations using specific Oracle EBS versions should check their patch status, look for indicators of compromise, and ensure their security controls are up to date.
This incident underscores the necessity of collective security responsibility among vendors, customers, and researchers. Organizations must evolve their defensive strategies from reactive to proactive, treating this event as an opportunity for significant security transformation.















