The cybersecurity landscape of 2025 has been marked by an unprecedented surge in vulnerability exploitation, with threat actors leveraging critical flaws across enterprise software, cloud infrastructure, and industrial systems.
This comprehensive analysis examines the twenty most dangerous exploited vulnerabilities of the year, highlighting their technical details, exploitation methods, and the urgent need for organizations to prioritize patching and defense strategies.
These vulnerabilities represent a combined CVSS severity rating averaging 8.5, with two achieving the maximum score of 10.0, underscoring the critical nature of these security flaws.
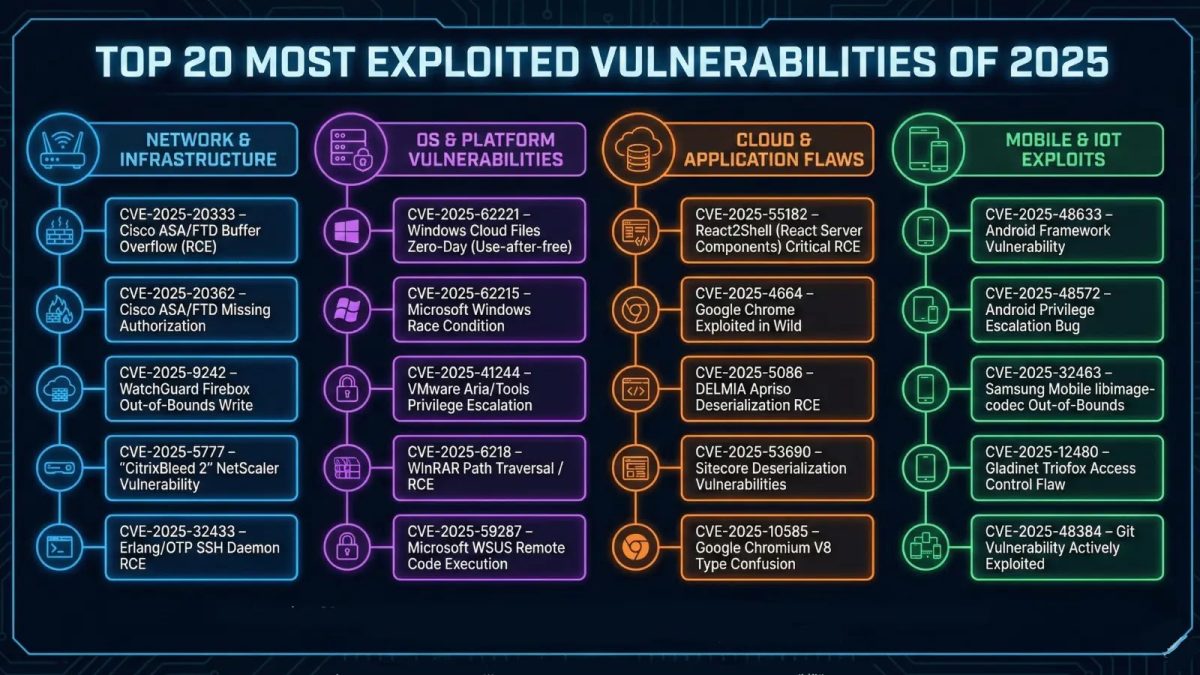
Table Detailing Most Exploited Vulnerabilities of 2025
| CVE ID | Vulnerability Title | CVSS v3.1 Score | Affected Product | Vulnerability Type | Authentication Required | Active Exploitation | Disclosure Date | CISA KEV Status | Primary Attack Vector |
|---|---|---|---|---|---|---|---|---|---|
| CVE-2025-55182 | React2Shell – React Server Components RCE | 10.0 (Critical) | React Server Components (Meta) | Deserialization / Unauthenticated RCE | No (Unauthenticated) | Yes – Mesh Agent Malware, Cryptocurrency Miners | December 3, 2025 | Added December 2025 | Network / Web Application |
| CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Use-After-Free | 7.8 (High) | Windows Cloud Files Mini Filter Driver | Use-After-Free / Memory Corruption | Yes (Authenticated Local) | Yes – Patch Tuesday December 2025 | December 9, 2025 | Added December 2025 | Local System Access |
| CVE-2025-6218 | WinRAR Path Traversal Remote Code Execution | 7.8 (High) | WinRAR 7.11 and earlier | Path Traversal / Arbitrary File Extraction | No (Unauthenticated – Archive File) | Yes – APT-C-08, GOFFEE, Bitter Groups | March 2025 / June 2025 Patch | Added December 2025 | User Interaction (Archive File) |
| CVE-2025-48633 | Android Framework Information Disclosure | High (Not Specified) | Android 13-16 Framework | Information Disclosure / Sandbox Bypass | No (Malicious App) | Yes – State Actors (Limited Targeted) | December 2, 2025 | Added December 2025 | Mobile Application / Malicious App |
| CVE-2025-48572 | Android Framework Privilege Escalation | High (Not Specified) | Android 13-16 Framework | Privilege Escalation / Unauthorized Activity | No (Malicious App) | Yes – State Actors (Limited Targeted) | December 2, 2025 | Added December 2025 | Mobile Application / Malicious App |
| CVE-2025-5777 | CitrixBleed 2 – Citrix NetScaler Memory Disclosure | 9.3 (Critical) | Citrix NetScaler ADC/Gateway | Out-of-Bounds Read / Session Hijacking | No (Unauthenticated) | Yes – RansomHub, Multiple Threat Groups | June 17, 2025 | Added July 2025 (24-hr deadline) | Network / VPN Gateway |
| CVE-2025-48384 | Git Arbitrary File Write on Non-Windows Systems | 8.0-8.1 (High) | Git on macOS and Linux | Arbitrary File Write / Git Hook Execution | No (Unauthenticated – Repository Clone) | Yes – Sophisticated Social Engineering | July 8, 2025 | Added August 2025 | Network / Git Repository |
| CVE-2025-41244 | VMware Aria Tools Local Privilege Escalation | 7.8 (High) | VMware Aria Operations, VMware Tools | Untrusted Search Path / LocalPrivEsc | Yes (Local User) | Yes – State Actor UNC5174 (Chinese APT) | September 29, 2025 | State Actor Exploitation (Not KEV) | Local System Access |
| CVE-2025-9242 | WatchGuard Firebox IKEv2 Out-of-Bounds Write | 9.3 (Critical) | WatchGuard Firebox (Fireware OS) | Out-of-Bounds Write / Stack Overflow | No (Unauthenticated) | Yes – Confirmed KEV Listing | September 17, 2025 | Added November 2025 | Network / VPN IKEv2 Protocol |
| CVE-2025-12480 | Gladinet Triofox Improper Access Control | 9.1 (Critical) | Gladinet Triofox | Improper Access Control / Authentication Bypass | No (Unauthenticated) | Yes – UNC6485 Cluster | November 12, 2025 (Public) | Added November 2025 | Network / HTTP Access |
| CVE-2025-62215 | Windows Kernel Race Condition Privilege Escalation | 7.0 (High) | Windows Kernel (All Supported OS) | Race Condition / Double Free Heap Corruption | Yes (Authenticated Local) | Yes – Confirmed KEV Listing | November 11, 2025 | Added November 2025 | Local System Access |
| CVE-2025-4664 | Google Chrome Cross-Origin Data Leak | 8.8 (High) | Google Chrome | Cross-Origin Data Leak / Referrer Policy Bypass | No (Unauthenticated – User Interaction) | Yes – Confirmed KEV Listing | May 14, 2025 | Added May 2025 | Network / Web Browser |
| CVE-2025-59287 | Microsoft WSUS Deserialization Remote Code Execution | 9.8 (Critical) | Microsoft WSUS (Windows Server Update Services) | Unsafe Deserialization / Gadget Chain RCE | No (Unauthenticated) | Yes – Widespread Exploitation POC | October 23, 2025 (Emergency Patch) | Added October 2025 | Network / WSUS Port 8530/8531 |
| CVE-2025-32463 | Sudo Chroot Privilege Escalation | 9.3 (Critical) | Sudo 1.9.14-1.9.17 | Relative Path Traversal / Privilege Escalation | Yes (Local User) | Yes – Confirmed KEV Listing | June 2025 | Added October 2025 | Local System Access |
| CVE-2025-20333 | Cisco ASA/FTD Buffer Overflow Remote Code Execution | 9.9 (Critical) | Cisco ASA/FTD | Buffer Overflow / VPN Authentication Bypass | Yes (Authenticated VPN) | Yes – ArcaneDoor (UAT4356) State Sponsor | September 24, 2025 | Added September 2025 (Emergency Directive) | Network / VPN Authentication |
| CVE-2025-20362 | Cisco ASA/FTD Missing Authorization Authentication Bypass | 6.5 (Medium) | Cisco ASA/FTD | Missing Authorization / Access Control Flaw | No (Unauthenticated) | Yes – ArcaneDoor Chain with CVE-2025-20333 | September 24, 2025 | Added September 2025 (Emergency Directive) | Network / Firewall Management |
| CVE-2025-10585 | Google Chrome V8 Type Confusion Remote Code Execution | 8.8 (High) | Google Chrome | Type Confusion / Memory Corruption RCE | No (Unauthenticated – User Interaction) | Yes – Google TAG Confirmed | September 16, 2025 | Added September 2025 | Network / Web Browser |
| CVE-2025-5086 | DELMIA Apriso Deserialization of Untrusted Data RCE | 9.0 (Critical) | DELMIA Apriso (2020-2025 Release) | Unsafe Deserialization / Gadget Chain RCE | No (Unauthenticated) | Yes – SANS ISC Observed | June 2, 2025 (Patch), September 11 (KEV) | Added September 2025 | Network / HTTP SOAP Request |
| CVE-2025-53690 | Sitecore ViewState Deserialization Remote Code Execution | 9.0 (Critical) | Sitecore Experience Manager/Platform | ViewState Deserialization / Gadget Chain RCE | No (Unauthenticated – Known Machine Key) | Yes – Mandiant Threat Defense Confirmed | September 2, 2025 | Added September 2025 | Network / Web Application |
| CVE-2025-32433 | Erlang/OTP SSH Daemon Pre-Authentication RCE | 10.0 (Critical) | Erlang/OTP SSH Daemon | SSH Protocol Parsing / Pre-Auth RCE | No (Pre-Authentication) | Yes – OT Environment Targeting | April 16, 2025 | Confirmed Active Exploitation | Network / SSH Protocol |
Most Exploited Vulnerabilities of 2025
CVE-2025-55182: React2Shell
The most critical vulnerability of 2025, CVE-2025-55182, dubbed “React2Shell,” represents a watershed moment in web application security. Disclosed on December 3, 2025, by Meta, this unauthenticated remote code execution flaw in React Server Components achieved the maximum CVSS score of 10.0. The vulnerability stems from insecure deserialization within the React Server Components (RSC) Flight protocol, where the server processes RSC payloads without adequate validation.
According to Wiz Research, 39% of cloud environments contain vulnerable instances, making this one of the most widespread critical vulnerabilities in recent history.
The flaw affects React versions 19.0, 19.1.0, 19.1.1, and 19.2.0, as well as downstream frameworks like Next.js. Security researchers confirmed that default configurations are vulnerable, meaning standard Next.js applications created with create-next-app can be exploited without any code changes by developers.
Rapid7 validated working proof-of-concept exploits within 48 hours of disclosure, and by December 8, 2025, exploitation attempts were detected on honeypots worldwide.
The exploitation methodology involves crafting malicious RSC payloads that trigger server-side execution logic, allowing attackers to execute privileged JavaScript code with SYSTEM-level access. Organizations observed attackers deploying Mesh Agent malware and cryptocurrency miners via PowerShell commands executed through the vulnerability.
CVE-2025-32433: Erlang/OTP SSH Zero-Day Crisis
CVE-2025-32433 represents another maximum severity vulnerability (CVSS 10.0) affecting the Erlang/OTP SSH daemon, disclosed on April 16, 2025. This pre-authentication remote code execution flaw allows attackers to execute arbitrary code without completing the SSH authentication process, exploiting improper handling of SSH protocol messages during the pre-authentication phase.
The vulnerability affects Erlang/OTP versions 27.3.2 and earlier, 26.2.5.10 and earlier, 25.3.2.19 and earlier, and all versions from OTP 17.0 and older. Erlang/OTP is foundational technology used by organizations including Ericsson, Cisco, and WhatsApp, making this vulnerability particularly dangerous for telecommunications, messaging platforms, IoT infrastructure, and financial services.
Palo Alto Networks reported that between May 1 and May 9, 2025, exploitation attempts surged sharply, with 70% of observed detections coming from firewalls safeguarding operational technology environments. The attack methodology involves sending SSH_MSG_CHANNEL_OPEN messages before authentication to initiate session channels, followed by SSH_MSG_CHANNEL_REQUEST with malicious “exec” payloads. If the SSH daemon runs with elevated privileges such as root, successful exploitation grants complete system control.
CVE-2025-59287: Microsoft WSUS Deserialization Vulnerability
Microsoft Windows Server Update Services became a prime target in 2025 through CVE-2025-59287, a critical remote code execution vulnerability with a CVSS score of 9.8. Disclosed with an out-of-band emergency patch on October 23, 2025, this flaw stems from unsafe deserialization of untrusted data in the WSUS service.
The vulnerability allows unauthenticated attackers to send crafted requests to WSUS endpoints on ports 8530 and 8531, achieving code execution with SYSTEM privileges. According to Huntress and Unit 42, attackers exploited the flaw by targeting the GetCookie() endpoint and ReportingWebService, causing improper deserialization of AuthorizationCookie objects using insecure BinaryFormatter and SoapFormatter.
Initial exploitation was observed in the wild with process chains showing wsusservice.exe and w3wp.exe spawning cmd.exe and powershell.exe to execute Base64-encoded reconnaissance commands. Attackers collected information using whoami, net user /domain, and ipconfig /all commands, exfiltrating data to remote webhook endpoints.
The vulnerability was added to CISA’s Known Exploited Vulnerabilities catalog immediately following disclosure, with a public proof-of-concept exploit accelerating widespread attacks.
CVE-2025-62221: Windows Cloud Files Driver Zero-Day
Microsoft’s December 2025 Patch Tuesday included fixes for CVE-2025-62221, a use-after-free elevation of privilege vulnerability in the Windows Cloud Files Mini Filter Driver that was actively exploited as a zero-day. With a CVSS score of 7.8, this vulnerability allows authenticated local attackers to escalate privileges to the SYSTEM level without user interaction.
The flaw stems from a use-after-free condition where a program attempts to use a block of memory that has already been returned to system control. CISA confirmed active exploitation by adding the vulnerability to its Known Exploited Vulnerabilities catalog on December 9, 2025, mandating Federal Civilian Executive Branch agencies to apply updates by December 30, 2025.
Security researchers noted that the vulnerability is particularly dangerous because it affects the Cloud Files Mini Filter Driver, a core Windows component managing cloud storage integration, present even if applications like OneDrive, Google Drive, or iCloud aren’t installed.
The low attack complexity and minimal privilege requirements make exploitation accessible to many potential attackers, enabling threat actors to disable security tooling, access sensitive information, move laterally across networks, and establish persistent high-privilege access.
CVE-2025-62215: Windows Kernel Race Condition Zero-Day
November 2025’s Patch Tuesday addressed CVE-2025-62215, a race condition vulnerability in the Windows Kernel with a CVSS score of 7.0, actively exploited in the wild. The vulnerability, discovered by Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC), allows authenticated attackers with low-level privileges to elevate their access to SYSTEM-level privileges.
The race condition vulnerability involves concurrent execution using shared resources with improper synchronization (CWE-362). Attackers exploit this by running specially crafted programs that repeatedly provoke timing errors, forcing multiple threads to access the same kernel resource without proper synchronization. This confuses the kernel’s memory handling, causing it to free the same memory block twice, a “double free” condition that corrupts the kernel heap and provides attackers a path to overwrite memory and seize control of execution flow.
Security experts assess that CVE-2025-62215 is primarily being used after initial compromise via phishing, RCE, or sandbox escape to elevate privileges, harvest credentials, and move laterally. The vulnerability affects all currently supported Windows OS editions, including Windows 10, Windows 11, Windows Server 2019 through Windows Server 2025, and Windows 10 Extended Security Updates (ESU). CISA set a remediation date of December 3, 2025, for federal agencies.
CVE-2025-48572 and CVE-2025-48633: Android Framework Zero-Days
Google’s December 2025 Android Security Bulletin addressed over 100 vulnerabilities, including two high-severity zero-days in the Android Framework that CISA added to its KEV catalog on December 2, 2025. CVE-2025-48572 is an elevation of privilege vulnerability allowing malicious apps to launch unauthorized activities from the background without user interaction. CVE-2025-48633 is an information disclosure flaw enabling apps to access sensitive system memory, potentially bypassing Android’s sandboxing protections.
Both vulnerabilities affect Android versions 13 through 16 and have been confirmed under “limited, targeted exploitation” in the wild, likely by state actors or commercial surveillance tools targeting high-value individuals. CVE-2025-48633 exists in the hasAccountsOnAnyUser method of DevicePolicyManagerService.java, where a logic error allows attackers to add a Device Owner after provisioning, leading to local escalation of privilege. CVE-2025-48572 stems from a permissions bypass in the Android Frameworks Base package, allowing unauthorized background activity launches.
Security researchers note that these vulnerabilities are particularly dangerous when chained together, with CVE-2025-48633 used to exfiltrate sensitive data or escape the application sandbox, while CVE-2025-48572 is leveraged to gain system-level privileges. Federal agencies were mandated to apply patches by December 23, 2025.
CVE-2025-5777: CitrixBleed 2
CVE-2025-5777, dubbed “CitrixBleed 2” due to its similarities with the 2023 CitrixBleed vulnerability (CVE-2023-4966), represents a critical out-of-bounds read vulnerability in Citrix NetScaler ADC and Gateway with a CVSS score of 9.3. Disclosed on June 17, 2025, and added to CISA’s KEV catalog on July 11 with an unprecedented 24-hour patching deadline, this vulnerability allows attackers to leak sensitive memory data, including authentication tokens and session cookies.
The vulnerability affects NetScaler devices configured as Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. According to security researcher Kevin Beaumont, exploitation started as far back as mid-June 2025, with one of the IP addresses linked to RansomHub ransomware activity. GreyNoise data shows exploitation efforts originating from 10 unique malicious IP addresses located in Bulgaria, the United States, China, Egypt, and Finland over 30 days, primarily targeting the United States, France, Germany, India, and Italy.
Attackers send specially crafted HTTP requests to vulnerable Citrix appliances, which respond with chunks of memory containing session data. Using leaked session tokens, attackers can hijack active VPN sessions, bypass multi-factor authentication, and access internal systems without credentials. Horizon3.ai researchers identified suspicious changes in the nsppe binary (NetScaler Packet Parsing Engine) and discovered that configuration utilities administrators use to manage NetScaler Gateway endpoints also utilize vulnerable memory space, making session tokens belonging to the “nsroot” user vulnerable to theft.
CVE-2025-20333 and CVE-2025-20362: Cisco Firewall Exploitation Chain
Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) suffered from two critical vulnerabilities exploited in the wild as zero-days before patches became available. CVE-2025-20333, with a CVSS score of 9.9, is a buffer overflow vulnerability in the VPN web server component, allowing authenticated attackers to execute arbitrary code as root. CVE-2025-20362, with a CVSS score of 6.5, is a missing authorization vulnerability enabling unauthenticated attackers to access restricted URL endpoints.
CISA issued Emergency Directive 25-03 on September 25, 2025, confirming active exploitation and widespread scanning. The agency attributed exploitation to the same threat actor behind ArcaneDoor (UAT4356), a state-sponsored espionage campaign first observed in 2024. The U.K. National Cyber Security Centre (NCSC) reported attacks delivering malware such as RayInitiator and LINE VIPER.
The exploitation chain involves attackers using CVE-2025-20362 to bypass authentication through crafted HTTP(S) requests, then chaining it with CVE-2025-20333 to achieve root-level remote code execution. On November 5, 2025, Cisco warned of a new attack variant causing unpatched devices to unexpectedly reload, leading to denial-of-service conditions. The vulnerabilities affect Cisco ASA versions 9.16–9.23 and Cisco FTD versions 7.0–7.7.
CVE-2025-9242: WatchGuard Firebox Out-of-Bounds Catastrophe
WatchGuard Firebox firewalls faced critical exploitation through CVE-2025-9242, an out-of-bounds write vulnerability in the iked process of WatchGuard Fireware OS with a CVSS score of 9.3. Disclosed on September 17, 2025, and added to CISA’s KEV catalog on November 12, 2025, this vulnerability allows remote unauthenticated attackers to execute arbitrary code.
The vulnerability affects both mobile user VPN with IKEv2 and branch office VPN using IKEv2 when configured with a dynamic gateway peer. WatchTowr Labs researchers identified the flaw as a stack-based buffer overflow in 2025, noting the lack of modern exploit mitigations in the enterprise-grade appliance. The vulnerability affects Fireware OS versions 11.10.2 through 11.12.4_Update1, 12.0 through 12.11.3, and 2025.1.
Security analysis revealed suspicious changes within /usr/bin/iked, specifically in the ike2_ProcessPayload_CERT function where missing length validation allows attackers to overflow buffers with crafted IKEv2 packets. The unauthenticated portion of the IKE protocol consists of two initial packet exchanges, with the vulnerable code processed during IKE_SA_AUTH, meaning attackers need only deliver two packets to reach the vulnerable code path.
Because attack potential includes disabling security tooling, accessing sensitive information, moving laterally across networks, and establishing persistent high-privilege access, organizations were urged to prioritize patching outside normal patch cycles.
CVE-2025-6218: WinRAR Path Traversal Exploitation
WinRAR, one of the most popular file archiving utilities worldwide, suffered from CVE-2025-6218, a critical path traversal vulnerability with a CVSS score of 7.8 affecting versions 7.11 and earlier. Disclosed in March 2025 and patched in WinRAR 7.12 Beta 1 in June 2025, the vulnerability was added to CISA’s KEV catalog on December 10, 2025, following confirmation of active exploitation by multiple threat groups.
The vulnerability stems from improper path validation in WinRAR’s RARReadHeader and RARProcessFile routines, which fail to normalize or validate relative path components like ‘../’ and ‘..’. Malicious archives containing crafted paths can extract files outside the intended folder, such as placing executables in the Windows Startup folder for automatic execution upon login. The flaw is exploitable whether the archive entry’s stored path is absolute or relative.
Multiple threat actors have been observed exploiting this vulnerability, including GOFFEE (Paper Werewolf), Bitter (APT-C-08/Manlinghua), and Gamaredon. SecPod researchers documented a targeted cyber-espionage campaign attributed to APT-C-08, focusing on government organizations in South Asia, using phishing emails with malicious RAR archives. The attack payload included a C# trojan designed to contact external servers for command-and-control, enabling keylogging, screenshot capture, RDP credential harvesting, and file exfiltration.
CVE-2025-48384: Git Arbitrary File Write Vulnerability
The widely used Git version control system faced exploitation through CVE-2025-48384, a high-severity vulnerability (CVSS 8.0–8.1) affecting macOS and Linux installations, disclosed on July 8, 2025. CISA added this vulnerability to its KEV catalog on August 26, 2025, with a remediation deadline of September 15, 2025, after confirming active exploitation.
The vulnerability stems from Git’s inconsistent handling of carriage return characters when parsing configuration files and submodule paths. When reading a config value, Git strips trailing carriage return and line feed (CRLF) characters, but when writing a config entry, values with a trailing CR are not quoted, causing the CR to be lost when the config is later read. Attackers craft malicious .gitmodules files with submodule paths ending in carriage returns, and when repositories are recursively cloned via git clone –recursive, the path parsing inconsistency allows arbitrary file writes to attacker-specified paths.
CrowdStrike identified active exploitation combining sophisticated social engineering tactics with malicious Git repository cloning operations. The exploitation involves strategically placing symlinks and leveraging carriage return confusion to write malicious content directly to the Git submodule’s hooks directory, which Git automatically executes as part of the normal submodule checkout process. DataDog researchers noted that the vulnerability could also be abused to overwrite victims’ Git configuration files, exfiltrating intellectual property such as proprietary source code to attacker servers transparently.
CVE-2025-12480: Gladinet Triofox Improper Access Control
Gladinet Triofox, an on-premises and hybrid file-sharing platform widely used by managed service providers and enterprises, suffered from CVE-2025-12480, an improper access control vulnerability with a CVSS score of 9.1. While Gladinet patched the flaw on July 26, 2025, in version 16.7.10368.56560, the vulnerability wasn’t publicly disclosed until November 12, 2025, when it was added to CISA’s KEV catalog following active exploitation observations.
Mandiant Threat Defense discovered that threat cluster UNC6485 exploited the flaw as early as August 24, 2025, nearly a month after the patch was released, but without public CVE disclosure. The vulnerability allows attackers to abuse HTTP Host header validation to access the management/AdminDatabase.aspx setup workflow, create native administrative accounts with no credentials, and then configure the product’s anti-virus executable path to run malicious scripts.
The exploitation chain involved modifying the Host header field to bypass access controls, successfully accessing AdminAccount.aspx, which redirects to InitAccount.aspx for creating new admin accounts. Once authenticated with the newly created Admin account, attackers uploaded malicious files and executed them using the built-in anti-virus feature, with the configured anti-virus path inheriting Triofox parent process privileges and running under the SYSTEM account context. Observed attack activity included deploying PLINK to tunnel RDP externally and downloading files to staging directories like C:\WINDOWS\Temp.
CVE-2025-32463: Sudo Privilege Escalation via Chroot
A critical vulnerability (CVSS 9.3) was discovered in Sudo versions 1.9.14 through 1.9.17, reported by Rich Mirch from Stratascale Cyber Research Unit in June 2025. CVE-2025-32463 allows local users to obtain root access by exploiting the –chroot option, where /etc/nsswitch.conf from a user-controlled directory is used.
The vulnerability stems from a change introduced in sudo 1.9.14 that allowed path resolution via chroot() using a user-specified root directory while the sudoers file was still being evaluated. An attacker could prepare a writable directory (for example under /tmp), place a fake /etc/nsswitch.conf and a malicious libnss_*.so library there, then invoke sudo with the –chroot option, causing sudo to load the attacker’s code with root privileges.
Major Linux distributions, including Ubuntu, Red Hat, SUSE, and Debian, issued security advisories and patches. The vulnerability was fixed in sudo version 1.9.17p1, reverting the change from sudo 1.9.14 and marking the chroot feature as deprecated. CISA added the vulnerability to its KEV catalog in October 2025, emphasizing the severity for enterprise Linux environments.
CVE-2025-4664: Chrome Cross-Origin Data Leak
Google Chrome was exploited via CVE-2025-4664, a high-severity vulnerability (CVSS 8.8) affecting versions prior to 136.0.7103.113, which was disclosed and patched on May 14, 2025. CISA added the vulnerability to its KEV catalog on May 15, 2025, with a remediation due date of June 5, 2025, confirming active exploitation.
The vulnerability stems from insufficient policy enforcement in the Chrome Loader component, allowing remote attackers to leak cross-origin data through crafted HTML pages. The issue lies in how Chrome handles the Link HTTP header on sub-resource requests such as images and scripts, honoring the referrer-policy directive even on sub-resources behavior not shared by other major browsers. Attackers can abuse this header by setting a looser policy like unsafe-url, causing Chrome to leak full referrer URLs including sensitive tokens or credentials to third-party domains.
Security researcher Vsevolod Kokorin (“slonser_”) noted that the Link header can set a referrer-policy with unsafe-url specification, capturing full query parameters that can contain sensitive data. In OAuth flows, this might lead to account takeover, as developers rarely consider the possibility of stealing query parameters via an image from a third-party resource. The vulnerability required user interaction (opening malicious HTML pages), but that step is relatively easy to achieve through phishing or compromised websites.
CVE-2025-10585: Chrome V8 Type Confusion Zero-Day
Google released emergency security updates in September 2025 to address CVE-2025-10585, an actively exploited type confusion vulnerability in the V8 JavaScript and WebAssembly engine. Discovered and reported by Google’s Threat Analysis Group (TAG) on September 16, 2025, the vulnerability achieved a high-severity rating and was confirmed under active exploitation.
Type confusion vulnerabilities occur when Chrome doesn’t verify the object type it’s handling and uses it incorrectly, mistaking one type of data for another, like treating a list as a single value or a number as text. This can cause unpredictable behavior and allow attackers to manipulate memory and run code remotely through crafted JavaScript on malicious or compromised websites. The vulnerability affects Chrome versions prior to 140.0.7339.185/.186 on Windows/macOS and 140.0.7339.185 on Linux.
CVE-2025-10585 represents the sixth Chrome zero-day publicly tied to active exploitation in 2025, following CVE-2025-2783, CVE-2025-4664, CVE-2025-5419, CVE-2025-6554, and CVE-2025-6558. Security researchers emphasized that type confusion bugs in V8 are particularly powerful, as tricking the engine into misinterpreting memory layout allows attackers to corrupt memory, crash the browser, or gain code execution on the host, all just by getting users to load malicious pages or content. Because proof-of-concept exploits were available, unpatched systems faced immediate risk from widespread exploitation attempts.
CVE-2025-5086: DELMIA Apriso Deserialization Catastrophe
Dassault Systèmes’ DELMIA Apriso manufacturing operations management platform suffered from CVE-2025-5086, a critical deserialization of untrusted data vulnerability with a CVSS score of 9.0. The vulnerability affects DELMIA Apriso versions from Release 2020 through Release 2025 and was patched on June 2, 2025, but not before active exploitation began.
CISA added the vulnerability to its KEV catalog on September 11, 2025, after the SANS Internet Storm Center reported observing real-world exploitation attempts on September 3, 2025. The vulnerability allows remote, unauthenticated attackers to execute arbitrary code without authentication through malicious SOAP/HTTP requests to vulnerable endpoints. Security researcher Johannes Ullrich observed attacks originating from IP address 156.244.33[.]162, with payloads consisting of Base64-encoded, GZIP-compressed .NET executables embedded within XML.
The malicious payload has been identified as a Windows executable classified by researchers as “Trojan.MSIL.Zapchast.gen,” a program designed for cyber espionage activities including keylogging, screenshot capture, and gathering active application lists. DELMIA Apriso is utilized in production processes for digitalization and monitoring, with widespread deployment in automotive, aerospace, electronics, high-tech, and industrial machinery sectors, supporting functions including production scheduling, quality management, resource allocation, and warehouse management. The exploitation represents a significant threat to operational technology environments and manufacturing critical infrastructure.
CVE-2025-41244: VMware Privilege Escalation by State Actors
VMware Aria Operations and VMware Tools contained CVE-2025-41244, a local privilege escalation vulnerability with a CVSS score of 7.8 that was exploited by state-linked actors before public disclosure. The vulnerability was disclosed on September 29, 2025, but NVISO researchers confirmed that sophisticated Chinese state-sponsored threat actor UNC5174 had been covertly leveraging the flaw since at least mid-October 2024.
The vulnerability affects systems with VMware Tools installed and managed by Aria Operations with Service Discovery Management Pack (SDMP) enabled, allowing malicious local actors with non-administrative privileges to escalate privileges to root on the same VM. The flaw exists in the service discovery feature within the get-versions.sh shell script’s get_version function, which uses broad-matching regular expressions that can match non-system binaries in user-writable directories, leading to untrusted search path vulnerabilities (CWE-426).
When successfully exploited, attackers gain elevated privileges, enabling complete control over affected systems. The vulnerability impacts VMware Aria Operations versions prior to 8.18.5, VMware Cloud Foundation Operations versions prior to 9.0.1.0, and VMware Tools versions prior to 13.0.5.0, 13.0.5, and 12.5.4. Broadcom’s failure to disclose active exploitation at the time of the advisory drew criticism from the cybersecurity community, with researchers emphasizing that organizations were left unaware of the real-world threat level.
CVE-2025-53690: Sitecore Deserialization Attacks
Sitecore Experience Manager (XM) and Experience Platform (XP) faced critical exploitation through CVE-2025-53690, a deserialization of untrusted data vulnerability (CVSS 9.0) affecting versions through 9.0. Mandiant Threat Defense discovered active ViewState deserialization attacks leveraging a sample machine key that had been exposed in Sitecore deployment guides from 2017 and earlier.
The vulnerability affects customers who deployed any version of multiple Sitecore products using the sample key exposed in publicly available deployment guides, specifically Sitecore XP 9.0 and Active Directory 1.4 and earlier versions. Sitecore confirmed that updated deployments automatically generate unique machine keys and notified affected customers. The vulnerability enables attackers to inject and execute arbitrary code by exploiting insecure deserialization of untrusted data.
Initial compromise was achieved by exploiting the ViewState Deserialization vulnerability on affected internet-facing Sitecore instances, resulting in remote code execution. A decrypted ViewState payload contained WEEPSTEEL malware designed for internal reconnaissance. Following successful exploitation, threat actors archived the root directory of the web application to obtain sensitive files such as web.config, deployed EARTHWORM network tunnel tools, DWAGENT remote access tools, and SHARPHOUND Active Directory reconnaissance tools. The attackers created local administrator accounts, dumped SAM/SYSTEM registry hives to compromise cached administrator credentials, and enabled lateral movement via RDP.
The twenty most exploited vulnerabilities of 2025 demonstrate the evolving sophistication of threat actors and the persistent challenges organizations face in securing modern IT infrastructure. With an average CVSS score of 8.5 and multiple vulnerabilities achieving the maximum severity rating of 10.0, these flaws represent critical risks to enterprise security posture.
Several key trends emerge from this analysis. First, deserialization vulnerabilities continue to plague enterprise applications, accounting for six of the twenty most exploited flaws (CVE-2025-55182, CVE-2025-59287, CVE-2025-5086, CVE-2025-53690).
Second, privilege escalation vulnerabilities targeting operating system kernels and drivers remain attractive to attackers seeking to establish persistent access (CVE-2025-62221, CVE-2025-62215, CVE-2025-48572, CVE-2025-48633, CVE-2025-41244, CVE-2025-32463).
Third, network infrastructure devices, including firewalls, VPNs, and gateways, face persistent targeting by state-sponsored actors (CVE-2025-5777, CVE-2025-20333, CVE-2025-20362, CVE-2025-9242).
Organizations must adopt a multi-layered defense strategy, prioritizing several key actions. Immediate patching of systems exposed to the internet or handling untrusted data should be the highest priority, particularly for maximum severity vulnerabilities like CVE-2025-55182 and CVE-2025-32433.
Implementation of network segmentation to isolate critical systems and limit lateral movement opportunities is essential, especially for operational technology environments vulnerable to CVE-2025-5086 and CVE-2025-41244. Enhanced monitoring and logging to detect exploitation attempts, particularly for deserialization attacks and privilege escalation behaviors, provides critical early warning capabilities.
Federal agencies must comply with CISA KEV catalog deadlines, with all twenty vulnerabilities either already added to the catalog or confirmed under active exploitation. Private sector organizations should treat KEV additions as urgent security priorities requiring accelerated patch deployment outside normal maintenance windows.
The rapid exploitation timelines observed in 2025, with proof-of-concept exploits appearing within hours of disclosure for CVE-2025-55182 and CVE-2025-48384, underscore the critical importance of proactive security postures and prepared incident response capabilities.
As the cybersecurity landscape continues to evolve, organizations must recognize that vulnerability management is not merely a technical challenge but a strategic imperative requiring executive attention, adequate resource allocation, and continuous vigilance.
The exploitation trends observed in 2025 will likely continue into 2026, with threat actors increasingly targeting supply chain dependencies, cloud infrastructure, and operational technology systems. Only through comprehensive defense-in-depth strategies, timely patching, and continuous monitoring can organizations hope to mitigate the risks posed by these critical vulnerabilities.